Dengan modal sedikit, telah bisa melaksanakan registrasi akun gacor dan memenangkan jackpot yang tersedia di web kami. Cuma dengan modal kecil 10rb saja dengan 1 ID optimis telah bisa mainkan semua permainan yang ada. Web slot gacor dana atau judi slot gacor dewaslot777 online deposit dana mendapatkan bet kecil untuk semua permainan yang tersedia di web Slot Dana dan menjadi alternatif terbaik sebagai web terpercaya.
Playtech telah berperan besar didalam menjual sekalian memperkenalkan judi slot pada segala pemggemar slot yang terdapat di penjuru dunia. Penyedia game dewa slot 777 yang satu ini adalah produsen game populer seperti Age of the Gods Goddess of Wisdom, Geisha Story, Amazon Wild, Suicide Squad, dan masih banyak lagi. Playtech juga adalah rival dari pragmatic didalam memberikan game dewa slot 777 dengan aturan sederhana sehingga gampang sekali untuk dimenangkan.
Bermain dimalam hari apakah lebih besar peluang untuk menang dibandingkan siang hari? Kami dapat katakan Iya! karena kami sudah menjalankan survei bermain pada ketika siang hari dan malam hari. Karenanya kami coba memang malam hari lebih memiliki tingkat kemenangan lebih tinggi dibanding siang hari, secara khusus pada ketika jam 22:00 WIB ke atas.
game slot amat populer, masih ada beberapa pemain judi yang tetap setia dengan game judi lainnya. 6 Game Judi Resmi Terbaik dan Terbesar di IndonesiaSitus judi online terbesar dan terlengkap Slot777 tentunya tak hanya menyediakan game Slot Resmi Slot777 saja. Kami selaku bandar judi online terpercaya juga menyediakan bermacam macam permainan judi online lainnya.
Ini tidak mengherankan sebab cabang olahraga ini memiliki jumlah penggemar terbesar dibandingi dengan cabang olahraga lainnya. Cukup menebak regu juara dalam suatu perlombaan sepak bola, maka Anda akan menerima pembayaran kemenangan layak dengan odds yang diberikan. Anda bisa bertaruh pada sejumlah perlombaan sepak bola dari berbagai liga terbaik, seperti Liga Italia, Liga Inggris, Liga Spanyol, Liga Prancis, Liga Jerman, dan bermacam-macam liga lainnya dari semua dunia. Judi Bola di SBO
Web Slot777 menyediakan judi bola di SBO sebagai ragam taruhan olahraga yang populer.
PG Soft merupakan satu satu provider Slot Legal yang memiliki kantor di Valletta, Malta. Game slot yang terkenal dari PG Soft yakni Mahjong Ways, Mask Carnival & Rooster Rumble. Dengan mempunyai banyak permainan virtual yang amat mengasyikan dan asik membuat PG Soft menjadi sebuah pengembang game judi online yang familiar saat ini. Pocket Soft Gaming pertama kali berdiri pada tahun 2015 dan menjadi langkah awal perjalanan website judi slot terbaik yang satu ini.
Great Rhino Megaways memiliki winrate RTP menempuh 97.53% serta telah rupanya bahwa permainan dewa slot 777 ini sangatlah gampang untuk didapat kemenangannya. Game ini juga mempunyai visual grafis yang luar awam sehingga selain bisa menguntungkan, juga akan memanjakan mata para peminatnya.
Game yang tenar dari Slot88 yaitu Winter Sweets, Dragons Reaum dan Thug Life. Slot88 merupakan sebuah situs Slot Legal Slot777 terbaru 2021, mengedepankan permainan yang mempunyai sistem bertaruh cukup stabil, visual serta background musik yang amat menyenangkan. Menangkan Jackpot Terbesar dalam permainan Slot Legal Slot777 resmi di Slot88. Slot88 bisa anda mainkan dan nikmati melalui 1 situs saja sehingga bisa memainkannya dimana saja dan kapan saja.
Situs Judi Slot terupdate dan terpercaya slot gacor dewaslot777 Dewa Slot777 menyediakan bermacam-macam macam game slot online uang autentik Indonesia dari provider agen atau bandar casino dewa slot online terbesar juga terpopuler di Asia. Salah satu bentuk layanan yang ditawarkan yaitu tautan slot online terupdate dimana bertujuan mempermudah dalam mengakses SITUS JUDI SLOT ONLINE GAMPANG MENANG TERPERCAYA 2022.
Berikut ini Link Kumpulan 10 Daftar Nama Website Judi Slot Situs Legal Gampang Menang Terkini dan Terpercaya 2022 Indonesia dari Agen Casino Terbaik slot gacor Dewa Slot777 :
SITUS JUDI SLOT ONLINE TERPERCAYA PRAGMATICPLAY
SITUS JUDI SLOT TERPERCAYA SPADEGAMING
SITUS SLOT ONLINE TERPERCAYA HABANERO
SITUS SLOT TERPERCAYA JOKER123
SITUS JUDI SLOT TERBAIK DAN TERPERCAYA NO 1 MICROGAMING
SITUS SLOT TERBAIK DAN TERPERCAYA TOP TREND GAMING
SITUS SLOT ONLINE TERPERCAYA INDONESIA ISOFTBET
SITUS SLOT ONLINE TERBAIK DAN TERPERCAYA PLAYTECH
SITUS AGEN JUDI SLOT ONLINE TERPERCAYA CQ9
SITUS BANDAR JUDI SLOT TERBAIK PLAY N GO
Web Agen Judi Slot Terkini dan Terpercaya 2022 slot gacor Dewa Slot777 benar-benar mudah untuk anda dapatkan di Google, game judi online terlengkap dan terlaris bisa dimainkan oleh banyak bettor profesional tiap-tiap harinya karena Situs Judi Laman slot gacor Dewa Slot777 sudah terpercaya. Kecuali itu slot gacor Dewa Slot777 akan senantiasa memberikan pelayanan profesional kepada anggota loyal game slot online terbaik. Disana anda dapat menemukan berbagai variasi permainan game judi online deposit pulsa terpopuler.
Sebab pandemi yang melanda di seluruh dunia sehingga menyebabkan banyak sekali kebutuhan masyarakat untuk berkerja dari rumah sehingga pengaplikasian komputerisasi atau work from home semakin membutuhkan keberadaan Internet. Kalian seharusnya mencoba bermain dan daftar slot di laman judi slot terpercaya 2022 kami. Tentunya hal itu dikarenakan sebab banyak sekali masyrakat Indonesia yang ketika ini berdiam diri dirumah sebab kerja di rumah. Oleh sebab itulah Euforia Game Judi Slot Website Terbaik di 2022 Indonesia di Laman Judi Slot Website Terpercaya slot gacor Dewa Slot777 mendadak popular/trending. Akan hal hal yang demikian, dengan adanya game slot terbaru dan terbaik menjadi salah satu permainan judi online yang gampang menang dan bisa menjadi penghasilan tambahan situasi ketika ini.
Web slot gacor Dewa Slot777 siapkan banyak permainan judi online uang asli yang menarik dari berbagai provider yang ada disana. So lantas saja bergabung bersama bandar atau Situs Judi Slot Web Gampang Menang Terpercaya 2022 Terkini di Indonesia 2022? Dan ada permainan slot online terjago yang gampang untuk dimenangkan yang dapat membantu melepas penat berakhir beraktivitas seharian. Dari sekian banyaknya bandar judi online uang orisinil yang ada di Indonesia, di bermacam review forum atau analitik dari para bettor kumpulan web slot online terbaik dan terpercaya 2022 posisi pertama ditempati oleh slot gacor dewa slot 777 Dewa Slot777 .
Track record dan reputasi Web Judi Slot Web Terpercaya 2022 slot gacor Dewa Slot777 sudah tak perlu diragukan lagi sebagai bandar JUDI ONLINE bagi para bettor kaum millenial. Kalian dapat mengenal atau cek sendiri melalui Pencarian di Google atau social media (Instagram, Facebook, Youtube, dan Twitter). Situs tipe taruhan bola dan slot, ada juga game judi online lainnya. Mudah ketinggalan, diantaranya ada dan permainan baru populer lainnya yang tersedia di SItus Judi Slot Web slot gacor Dewa Slot777 . Tentunya slot gacor Dewa Slot777 menawarkan game JUDI ONLINE terpopuler dan terlaris lainnya. Kami selaku website slot online terbaik 2022 sekalian daftar bandar bola online terpercaya SBOBET merupakan slot gacor Dewa Slot777 layaknya bintang lima.
Website slot gacor Dewa Slot777 yang telah diketahui sebagai agen bola terbaik dan terbaru 2022 dari website judi slot online terpercaya slot gacor Dewa Slot777 . Ada banyak sekali game judi slot gacor hari ini mudah menang yang dapat anda mainkan di website judi slot terbaik dan terpercaya no 1 diantara lainnya merupakan :
Slot Laman Pragmatic Play
Slot Laman Live22
Slot88 & Slot888
Slot Situs Iconic Gaming
Slot gacor DEWA SLOT 777 Dewa Slot777
Slot Situs PG Soft
Slot Web Joker123
Slot Situs Spadegaming
Slot Laman JDB
Slot Situs Playtech
Slot Laman Microgaming
Slot Website Habanero
Slot Laman CQ9
Slot Website YGGDRASIL
Slot Web Play’n Go
Slot Situs One Touch Gaming
Slot Laman RTG Slots
Slot Website Flow Gaming
Slot Web Gamatron
Slot Website Advant Play
Di slot gacor Dewa Slot777 website judi slot gacor dewa slot 777 hari ini terpercaya kencang menang juga hadirkan judi layanan judi slot online deposit melalui pulsa Telkomsel dan juga layanan deposit melewati e-money Dana, Ovo, LinkAja, Gopay. Sebagai salah satu website slot online terbaik 2022 sekaligus kumpulan website judi bola terpercaya di indonesia semenjak tahun 2019 — 89. Kini ini, banyak orang yang telah daftar judi slot terupdate bergabung dan merasakan keuntungan ketika bermain di website judi slot online mudah menang terpercaya slot gacor Dewa Slot777 . Bagi member slot online, kau akan mendapatkan seluruh game judi onlnie terupdate dari kami yaitu 9Gaming, dengan tampilan yang baru dan ada fitur menarik, serta bonus jackpot slot online terbesar.
Dengan berbagai Benefit lainnya dari Web Slot Web Terpercaya, adalah:
daftar slot gacor 2022 terbaik yang betul-betul mudah dilaksanakan
Withdraw dan Deposit praktis dan sederhana
mencoba demo joker123 khususnya dahulu
Membayar setiap kemenangan pemain
Menyediakan laman judi slot gacor terbaru promo terupdate 2022.
Daftar Nama Nama Game Judi Slot Gacor 2022 Website Terbaik Dan Terpercaya No 1 2022
Berikut yakni kumpulan nama nama situs khusus judi slot online terpercaya di Indonesia yang bekerjasama dengan , untuk menyediakan berjenis-jenis permainan game slot online uang asli terpopuler untuk anda mainkan:
Slot Gacor Pragmatic Play
Slot Gacor Live22
Slot88
Slot Gacor Iconic Gaming
Slot gacor Dewa Slot777
Slot Gacor PG Soft
Slot Gacor Joker123
Slot Gacor Spadegaming
Slot Gacor JDB
Slot Gacor Playtech
Slot Gacor Microgaming
Slot Gacor Habanero
Slot Gacor CQ9
Slot Gacor YGGDRASIL
Slot Gacor Play’n Go
Kumpulan Daftar Laman Judi Slot Web Terpercaya Indonesia 2022 — 2023
Website slot gacor Dewa Slot777 Selaku situs judi slot terbaik dan terpercaya no 1 menyediakan daftar website judi slot gacor 2022 bagi segala bettor judi slot online dengan menyediakan beraneka ragam game menyenangkan seperti poker, slot online online, live casino online dengan bonus jackpot terbesar. Mudah cuma itu, kami juga didukung layanan judi slot deposit bank lokal Bca, Bri, Bni dan Mandiri
Banyak malahan alternatif provider slot online gacor yang sering beri jackpot yang dapat anda mainkan bersama dan bonus jackpot slot online bisa anda dapatkan dengan mudah. Kalian bisa seketika memilih alternatif ragam game judi penghasil uang dengan cara daftar SBOBET bersama bandar bola online terbesar atau Website Judi Slot Terbaik dan Terpercaya no 1 slot gacor Dewa Slot777.
Web Slot Gacor Web Hari ini Gampang Menang dan Terbaik 2022
Website Judi Slot Gacor Gampang Menang dan Terbaik di Indonesia bersama slot gacor Dewa Slot777 slot online yang akan selalu memberikan fasilitas dan layanan terkemuka untuk para pemain slot gacor online Indonesia. Buat anda para pecinta slot jackpot besar dapat seketika kesini guna memenangkan tak sedikit sekali duit dengan cuma deposit sebesar sebesar 10 ribu rupiah saja.
Ada banyak bonus dan promosi yang bisa anda temukan saat bergabung dengan website judi slot online mudah menang, diantara lainnya seperti :
Bonus New Tautan
Bonus Referral
Bonus Rebate All Game
Turn Over Mingguan dan Bulanan
Daftar Laman Slot Situs Terbaik 2022 — 2023 Web Menang Jackpot
Slot gacor Dewa Slot777 Web laman judi slot online di indonesia yang terbaik dan paling gacor sehingga kepuasan bermain game slot online online akan tercipta apalagi kalau anda bergabung dengan yang menjadi salah satu agen slot online online terpercaya tahun 2022 — 2023.
Pastinya anda akan mujur dan dimanjakan dengan beraneka pelayanan yang tersedia. Jadi kamu dapat mendapatkan uang dengan gampang melewati judi online slot online online terpercaya, slot maupun poker.
Daftar Agen judi slot online Tergacor Indonesia Terlengkap 2022
Ada sebagian alasan kenapa member setia kami selalu bermain dan melakukan transaksi daftar slot online tergacor di tempat kami. Laman judi bola terbesar SBOBET slot gacor Dewa Slot777 . Berikut kelebihan kami yang akan diinformasikan seperti dibawah ini.
Pragmatic Play Slot
Joker Gaming
Spadegaming
RTG Slot
Flow Gaming
Microgaming
Playtech
Habanero Slot
PG Soft
Play’n Go
CQ9
Global Gaming
One Touch
SLOT88
SITUS JUDI ONLINE24JAM TERPERCAYA
Slot gacor Dewa Slot777 Laman situs slot gacor hari ini permainan judi online 24jam terpercaya yang menyediakan banyak ragam permainan judi seperti, taruhan bola, casino, poker online, tembak ikan, sabung ayam. Para pemain apabila bergabung menjadi member serta berjenis-jenis keuntungan menarik lain. Anda tak semestinya merasa repot lagi mencari web judi lain yang belum tentu dapat memberikan kemenangan. Situs slot online terbaik menghadirkan teknologi wallet yang membikin kemudahan dalam memainkan segala permainan dalam satu akun saja untuk bermain judi bola dan slot online.
Anda dapat memilih permainan cocok skill dan kesukaan anda, sehingga bisa membuat anda menerima banyak hadiah dan bonus sbobet88, semakin kerap kali bermain dan mengumpulkannya bisa membuat anda menjadi orang kaya dalam waktu yang singkat. Termasuk di dalamnya beraneka-macam game popular seperti: sbobet slot Gacor online, poker idn, 9Gaming Poker sudah disediakan untuk memenuhi kepuasan para anggota.
Slot online tergacor terlengkap dengan bonus terbaik. Alasannya adalah sebab agen slot Gacor ini telah lama dipercaya oleh ribuan pengguna dan kami juga melayani secara profesional dalam proses transaksi deposit ataupun withdraw bersama AGEN SBOBET ONLINE TERPERCAYA.
Berapapun kemenangan para bettor Dewa Slot 777 joker123 saat melaksanakan taruhan bersama agen slot online kami maka akan kami transfer dengan pesat dengan hanya memerlukan waktu beberapa menit saja. Sebab hanya dengan 1 akun anda sudah bisa memainkan semua variasi permainan judi24online terpercaya secara komplit. Anda bisa memilih segala variasi permainan slot dari provider games yang terbaik dengan layanan ramah selama 24 jam.
Anda dapat menemukan kemungkinan terbesar untuk dapat menang selama bermain jackpot slot. kami hanya menyediakan yang terbaik untuk siapa saja yang berharap bergabung dengan penawaran terbaik.
Oleh karena itu tentunya daftar bocoran slot gacor mudah menang juga selalu menyediakan kemungkinan menang yang lebih besar untuk anda selama memasang taruhan online uang absah.
SITUS JUDI SLOT ONLINE TERLENGKAP DAN TERBAIK 2022 DI INDONESIA
Banyak kemungkinan yang sudah disediakan selama memiliki harapan bermain Slot Situs di website judi terpercaya. penjelasannya sebagai berikut. Jadi tak perlu diragukan lagi, segala telah nampak di halaman depan laman kita Web Daftar Judi Slot Web Joker123 Deposit Pulsa.
SITUS JUDI SLOT ONLINE TERLENGKAP DAN TERBAIK 2022 DI INDONESIA
Kebanyakan orang bilang kans emas jangan pernah dilewatkan, ini lah saatnya anda seluruh dapat menerima profit dengan cara bermain di agen judi online terpercaya yang menyediakan daftar slot online dan register akun slot joker123 deposit pulsa paling lengkap di indonesia.
Bersama kalian akan menerima sensais bermain judi online slot Gacor yang betul-betul berbeda, pastinya betul-betul rekomen banget deh!! Website link slot gacor Indonesia tentunya menjadi salah satu yang paling dicari sehingga para pemain dapat memilih web Gacor yang kredibel dan terpercaya. Kini telah hadir dengan memberikan pelayanan terbaik sebagai laman judi slot terbaik dan online legal terkini & terpercaya no 1 di Indonesia.
Situs Daftar Judi Slot Web Terbaik Indonesia Deposit Pulsa
Website joker123 dan slot online deposit pulsa yang dilengkapi dengan ratusan tipe game taruhan judi online paling komplit, dimana cuma cukup dengan deposit 10 ribu saja anda seluruh telah berkesempatan untuk memenangkan jackpot uang hingga puluhan juta rupiah.
Selain itu fasilitas yang disediakan juga betul-betul komplit, bukan cuma menyediakan game judi slot online dengan tampilan terkini dan menarik, bonus yang kami sediakan juga dapat dibilang paling tinggi dan bukan hanya omongan belaka saja bersama website judi slot terbaru. Oleh sebab itu kami mengajak anda untuk seketika daftar saja seketika gan, tidak perlu tunggu dan ragu lagi.
sudah lengkap di wabsite yang satu ini, dan untuk mendapatkan akun dari juga betul-betul gampang sekali, dimana hanya perlu sebagian data yang memudahkan kami untuk melaksanakan transaksi saja di web judi slot online terpercaya. Apa saja fasilitas dan pelayanan sediakan? Dan hal hal yang demikian dapat anda lakukan melewati notebook, handphone, tablet, dan yang lainnya, jadi langsung ya gan ditunggu hadirnya di Agen Judi Daftar Game Slot Joker123 Indonesia.


 Размещение объявлений в телеграмм группах проще размещения в соц сетях и на других площадках. Это обусловлено тем, что телеграмм является мессенджером, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, ориентированная именно на такие сделки и в нужном Вам городе.
Размещение объявлений в телеграмм группах проще размещения в соц сетях и на других площадках. Это обусловлено тем, что телеграмм является мессенджером, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, ориентированная именно на такие сделки и в нужном Вам городе. Размещение объявлений в телеграмм результативнее размещения в соцсетях и на других сайтах. Это объясняется тем, что телеграм – мессенджер, это означает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, объявления бесплатно которая ориентирована именно на такие сделки и в нужном вам городе.
Размещение объявлений в телеграмм результативнее размещения в соцсетях и на других сайтах. Это объясняется тем, что телеграм – мессенджер, это означает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, объявления бесплатно которая ориентирована именно на такие сделки и в нужном вам городе. Размещение объявлений в телеграмм группах результативнее размещения в соц сетях и на других сайтах. Это обусловлено тем, что telegram – мессенджер, что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений –это целевая аудитория, бесплатные объявления ориентированная именно на такие сделки и в нужном вам городе.
Размещение объявлений в телеграмм группах результативнее размещения в соц сетях и на других сайтах. Это обусловлено тем, что telegram – мессенджер, что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений –это целевая аудитория, бесплатные объявления ориентированная именно на такие сделки и в нужном вам городе. In an era defined by digital connectivity, the term “cyber card hack” has emerged as a menacing challenge that threatens the security of electronic payments. They request personal information, passwords, or credit card details under false pretenses. Phishing: Scammers often send emails, messages, or calls posing as legitimate entities such as banks or government agencies. In conclusion, scammers employ a wide range of tactics to deceive and defraud individuals.
In an era defined by digital connectivity, the term “cyber card hack” has emerged as a menacing challenge that threatens the security of electronic payments. They request personal information, passwords, or credit card details under false pretenses. Phishing: Scammers often send emails, messages, or calls posing as legitimate entities such as banks or government agencies. In conclusion, scammers employ a wide range of tactics to deceive and defraud individuals. Black Market Demand: The underground market for stolen card data is robust. Cybercriminals sell card
Black Market Demand: The underground market for stolen card data is robust. Cybercriminals sell card  CVV shops are online platforms where cybercriminals offer stolen credit card data, including the Card Verification Value (CVV) numbers—the three or four-digit codes on the back of credit and debit cards.
CVV shops are online platforms where cybercriminals offer stolen credit card data, including the Card Verification Value (CVV) numbers—the three or four-digit codes on the back of credit and debit cards. Awareness and proactive action play pivotal roles in safeguarding personal finances and contributing to a more secure online ecosystem for all. The digital age has brought unprecedented convenience to financial transactions, but it has also given rise to new forms of cybercrime, including Western Union hack fraud. This article aims to shed light on the risks associated with Western Union hack fraud, explore how it occurs, and provide insights into prevention measures.
Awareness and proactive action play pivotal roles in safeguarding personal finances and contributing to a more secure online ecosystem for all. The digital age has brought unprecedented convenience to financial transactions, but it has also given rise to new forms of cybercrime, including Western Union hack fraud. This article aims to shed light on the risks associated with Western Union hack fraud, explore how it occurs, and provide insights into prevention measures. In conclusion, the world of hacking is a complex landscape with both positive and negative implications. Ethical hacking plays a crucial role in improving cybersecurity and fostering innovation, while malicious hacking poses significant risks to privacy, finances, and digital infrastructure. As technology continues to evolve, ethical hacking and responsible cybersecurity practices are essential in maintaining a safe and secure digital environment for individuals, businesses, and society as a whole.
In conclusion, the world of hacking is a complex landscape with both positive and negative implications. Ethical hacking plays a crucial role in improving cybersecurity and fostering innovation, while malicious hacking poses significant risks to privacy, finances, and digital infrastructure. As technology continues to evolve, ethical hacking and responsible cybersecurity practices are essential in maintaining a safe and secure digital environment for individuals, businesses, and society as a whole.

 Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities. A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Fraudsters aim to complete the series of unauthorized purchases before the initial authorization lapses or is flagged by the cardholder or financial institution.
Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities. A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Fraudsters aim to complete the series of unauthorized purchases before the initial authorization lapses or is flagged by the cardholder or financial institution. Understanding Scammers and Their Tactics: Scammers are individuals who use cunning strategies to trick people into giving away their money, personal information, or valuable assets. They exploit relationships to manipulate victims into providing money or sensitive information. Impersonation: Some scammers impersonate trusted individuals, such as tech support agents, family members, or friends.
Understanding Scammers and Their Tactics: Scammers are individuals who use cunning strategies to trick people into giving away their money, personal information, or valuable assets. They exploit relationships to manipulate victims into providing money or sensitive information. Impersonation: Some scammers impersonate trusted individuals, such as tech support agents, family members, or friends.
 Understanding the methods hackers employ, the implications of such breaches, and implementing strong cybersecurity practices are essential for safeguarding your financial information. Timing: The timing of transactions is critical. Fraudsters aim to complete the series of unauthorized purchases before the initial authorization lapses or is flagged by the cardholder or financial institution. Temporary Authorizations: When a cardholder makes a purchase, a temporary authorization is placed on their account to confirm that the card is
Understanding the methods hackers employ, the implications of such breaches, and implementing strong cybersecurity practices are essential for safeguarding your financial information. Timing: The timing of transactions is critical. Fraudsters aim to complete the series of unauthorized purchases before the initial authorization lapses or is flagged by the cardholder or financial institution. Temporary Authorizations: When a cardholder makes a purchase, a temporary authorization is placed on their account to confirm that the card is  A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities. The concept of an underground economy dedicated to fraudulent activities has gained notoriety as the “fraud economy.” This clandestine realm operates outside legal boundaries, involving various illicit activities such as identity theft, credit card fraud, counterfeit operations, and more.
A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities. The concept of an underground economy dedicated to fraudulent activities has gained notoriety as the “fraud economy.” This clandestine realm operates outside legal boundaries, involving various illicit activities such as identity theft, credit card fraud, counterfeit operations, and more. Understanding Cyber Card Hacks: A cyber card hack involves the unauthorized access, manipulation, or theft of sensitive payment card information for fraudulent purposes. Cybercriminals deploy various techniques to compromise digital transactions, posing risks to both consumers and businesses engaged in online commerce. Compliance: Some industries and regulations require strict security measures for processing payments.
Understanding Cyber Card Hacks: A cyber card hack involves the unauthorized access, manipulation, or theft of sensitive payment card information for fraudulent purposes. Cybercriminals deploy various techniques to compromise digital transactions, posing risks to both consumers and businesses engaged in online commerce. Compliance: Some industries and regulations require strict security measures for processing payments. This article aims to shed light on the risks associated with Western Union hack fraud, explore how it occurs, and provide insights into prevention measures. Awareness and proactive action play pivotal roles in safeguarding personal finances and contributing to a more secure online ecosystem for all. By staying informed, implementing preventive measures, and promptly reporting any suspicious activity, individuals can protect themselves from falling victim to these cybercrimes.
This article aims to shed light on the risks associated with Western Union hack fraud, explore how it occurs, and provide insights into prevention measures. Awareness and proactive action play pivotal roles in safeguarding personal finances and contributing to a more secure online ecosystem for all. By staying informed, implementing preventive measures, and promptly reporting any suspicious activity, individuals can protect themselves from falling victim to these cybercrimes. Understanding Fresh Clone Cards Fraud: Fresh Clone Cards fraud involves the creation and use of counterfeit credit or debit cards, commonly referred to as “clones.” These clones are crafted using stolen card data, often obtained from data breaches, phishing attacks, or compromised point-of-sale terminals. Conclusion: Fresh Clone Cards fraud represents a significant challenge in the digital age, posing risks to both individuals and businesses alike.
Understanding Fresh Clone Cards Fraud: Fresh Clone Cards fraud involves the creation and use of counterfeit credit or debit cards, commonly referred to as “clones.” These clones are crafted using stolen card data, often obtained from data breaches, phishing attacks, or compromised point-of-sale terminals. Conclusion: Fresh Clone Cards fraud represents a significant challenge in the digital age, posing risks to both individuals and businesses alike. Vishing, a variant, involves criminals using voice calls to manipulate individuals into revealing sensitive information. Phishing and Vishing: Phishing entails fraudsters sending deceptive emails or messages, impersonating legitimate organizations to obtain victims’ credit card information.
Vishing, a variant, involves criminals using voice calls to manipulate individuals into revealing sensitive information. Phishing and Vishing: Phishing entails fraudsters sending deceptive emails or messages, impersonating legitimate organizations to obtain victims’ credit card information. Understanding the Fraudulent Sale of PayPal and Bank Logins: The illicit sale of PayPal and bank logins involves the unauthorized access to individuals’ online payment accounts and financial institutions’ systems. Cybercriminals gain unauthorized entry through various methods, including phishing, malware, and hacking, and subsequently sell these stolen credentials on the dark web. In an era where digital convenience reigns supreme, online transactions have become an integral part of our daily lives.
Understanding the Fraudulent Sale of PayPal and Bank Logins: The illicit sale of PayPal and bank logins involves the unauthorized access to individuals’ online payment accounts and financial institutions’ systems. Cybercriminals gain unauthorized entry through various methods, including phishing, malware, and hacking, and subsequently sell these stolen credentials on the dark web. In an era where digital convenience reigns supreme, online transactions have become an integral part of our daily lives. By using credit cards wisely and understanding their terms, individuals can harness their benefits while avoiding potential pitfalls. However, it’s crucial to emphasize responsible usage, as improper handling of credit cards can lead to debt accumulation and financial strain. In conclusion, credit cards have transformed the way we manage money and conduct transactions. Their convenience, financial flexibility, rewards, security features, and educational value have made them an essential aspect of modern society.
By using credit cards wisely and understanding their terms, individuals can harness their benefits while avoiding potential pitfalls. However, it’s crucial to emphasize responsible usage, as improper handling of credit cards can lead to debt accumulation and financial strain. In conclusion, credit cards have transformed the way we manage money and conduct transactions. Their convenience, financial flexibility, rewards, security features, and educational value have made them an essential aspect of modern society. Размещение объявлений в telegram лучше размещения в социальных сетях и на других площадках. Это обусловлено тем, объявления бесплатно что телеграмм – мессенджер, что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений –это целевая аудитория, которая ориентирована именно на такие сделки и именно в нужном Вам городе.
Размещение объявлений в telegram лучше размещения в социальных сетях и на других площадках. Это обусловлено тем, объявления бесплатно что телеграмм – мессенджер, что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений –это целевая аудитория, которая ориентирована именно на такие сделки и именно в нужном Вам городе. In an increasingly digital world, where convenience is paramount and online transactions are the norm, the threat of CVV (Card Verification Value) fraud has become a significant concern for individuals and businesses alike. This article explores the ins and outs of CVV fraud and offers insights on how to safeguard yourself against this ever-evolving threat.
In an increasingly digital world, where convenience is paramount and online transactions are the norm, the threat of CVV (Card Verification Value) fraud has become a significant concern for individuals and businesses alike. This article explores the ins and outs of CVV fraud and offers insights on how to safeguard yourself against this ever-evolving threat. Among these activities, the sale of “fresh dumps pin (
Among these activities, the sale of “fresh dumps pin ( Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. Wired Data Links: These involve physical connections, such as Ethernet cables, fiber optics, or coaxial cables. They offer high-speed and reliable data transmission, making them suitable for both short and long distances.
Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. Wired Data Links: These involve physical connections, such as Ethernet cables, fiber optics, or coaxial cables. They offer high-speed and reliable data transmission, making them suitable for both short and long distances. Conclusion: CVV shops epitomize the darker aspects of the digital age, perpetuating fraud, identity theft, and financial losses. A united front involving governments, law enforcement, cybersecurity experts, and responsible online behavior is pivotal in curtailing the dark side of CVV shops and fostering a safer digital landscape for everyone. By understanding the risks, staying informed about evolving cybercrime tactics, and adopting stringent security measures, we can collectively work towards mitigating the impact of
Conclusion: CVV shops epitomize the darker aspects of the digital age, perpetuating fraud, identity theft, and financial losses. A united front involving governments, law enforcement, cybersecurity experts, and responsible online behavior is pivotal in curtailing the dark side of CVV shops and fostering a safer digital landscape for everyone. By understanding the risks, staying informed about evolving cybercrime tactics, and adopting stringent security measures, we can collectively work towards mitigating the impact of  Understanding Dumps Good
Understanding Dumps Good  In conclusion, online credit card transactions offer a world of convenience and access to a global marketplace. Hackers seek to steal credit card details to make unauthorized purchases, withdraw cash, or engage in identity theft. By gaining access to these accounts, cybercriminals can monetize the stolen data through fraudulent activities, transferring funds or making purchases before the victim becomes aware of the breach.
In conclusion, online credit card transactions offer a world of convenience and access to a global marketplace. Hackers seek to steal credit card details to make unauthorized purchases, withdraw cash, or engage in identity theft. By gaining access to these accounts, cybercriminals can monetize the stolen data through fraudulent activities, transferring funds or making purchases before the victim becomes aware of the breach. If you notice anything suspicious, report it to your bank or card issuer immediately. Regularly Monitor Your Accounts: Frequently review your bank and credit card statements to detect any unauthorized transactions promptly. Card-Not-Present (CNP) Fraud: CNP fraud occurs when a fraudster uses stolen credit card details to make online or phone transactions where the physical card is not required. Cybercriminals often target e-commerce websites, making unauthorized purchases by exploiting stolen card information.
If you notice anything suspicious, report it to your bank or card issuer immediately. Regularly Monitor Your Accounts: Frequently review your bank and credit card statements to detect any unauthorized transactions promptly. Card-Not-Present (CNP) Fraud: CNP fraud occurs when a fraudster uses stolen credit card details to make online or phone transactions where the physical card is not required. Cybercriminals often target e-commerce websites, making unauthorized purchases by exploiting stolen card information. Counterculture and Rebellion: For some, hacking represents a form of digital counterculture or rebellion against established norms. Conclusion: Selling Dumps Good Fresh is a grave manifestation of cybercrime, posing significant threats to both individuals and the integrity of digital transactions. By fostering a culture of cybersecurity awareness, implementing stringent preventive measures, and collaborating with law enforcement, individuals and businesses can collectively combat the menace of selling Dumps Good Fresh and work toward a safer and more secure digital landscape.
Counterculture and Rebellion: For some, hacking represents a form of digital counterculture or rebellion against established norms. Conclusion: Selling Dumps Good Fresh is a grave manifestation of cybercrime, posing significant threats to both individuals and the integrity of digital transactions. By fostering a culture of cybersecurity awareness, implementing stringent preventive measures, and collaborating with law enforcement, individuals and businesses can collectively combat the menace of selling Dumps Good Fresh and work toward a safer and more secure digital landscape.
 Impersonation and Social Engineering: Criminals often impersonate trustworthy figures, like tech support agents, family members, or colleagues, to manipulate individuals into giving away sensitive information or money. Social engineering exploits human psychology and relationships to deceive victims into taking actions they normally wouldn’t. In the realm of cybercrime, the term “fullz” refers to a complete set of stolen personal information, typically including names, addresses, Social Security numbers, and credit card details.
Impersonation and Social Engineering: Criminals often impersonate trustworthy figures, like tech support agents, family members, or colleagues, to manipulate individuals into giving away sensitive information or money. Social engineering exploits human psychology and relationships to deceive victims into taking actions they normally wouldn’t. In the realm of cybercrime, the term “fullz” refers to a complete set of stolen personal information, typically including names, addresses, Social Security numbers, and credit card details. Understanding Scammers and Their Tactics: Scammers are individuals who use cunning strategies to trick people into giving away their money, personal information, or valuable assets. In the intricate world of cybercrime, one disturbing trend that has emerged is the pursuit of “high valid
Understanding Scammers and Their Tactics: Scammers are individuals who use cunning strategies to trick people into giving away their money, personal information, or valuable assets. In the intricate world of cybercrime, one disturbing trend that has emerged is the pursuit of “high valid  CVV fraud occurs when cybercriminals gain unauthorized access to this code, allowing them to make fraudulent online purchases or withdrawals. Understanding CVV Fraud: The CVV code, a three- or four-digit number typically found on the back of a credit or debit card, is a crucial security feature designed to verify that the cardholder has the physical card in their possession during transactions. Avoid providing this information through emails or messages, as legitimate organizations will never ask for it via these channels.
CVV fraud occurs when cybercriminals gain unauthorized access to this code, allowing them to make fraudulent online purchases or withdrawals. Understanding CVV Fraud: The CVV code, a three- or four-digit number typically found on the back of a credit or debit card, is a crucial security feature designed to verify that the cardholder has the physical card in their possession during transactions. Avoid providing this information through emails or messages, as legitimate organizations will never ask for it via these channels.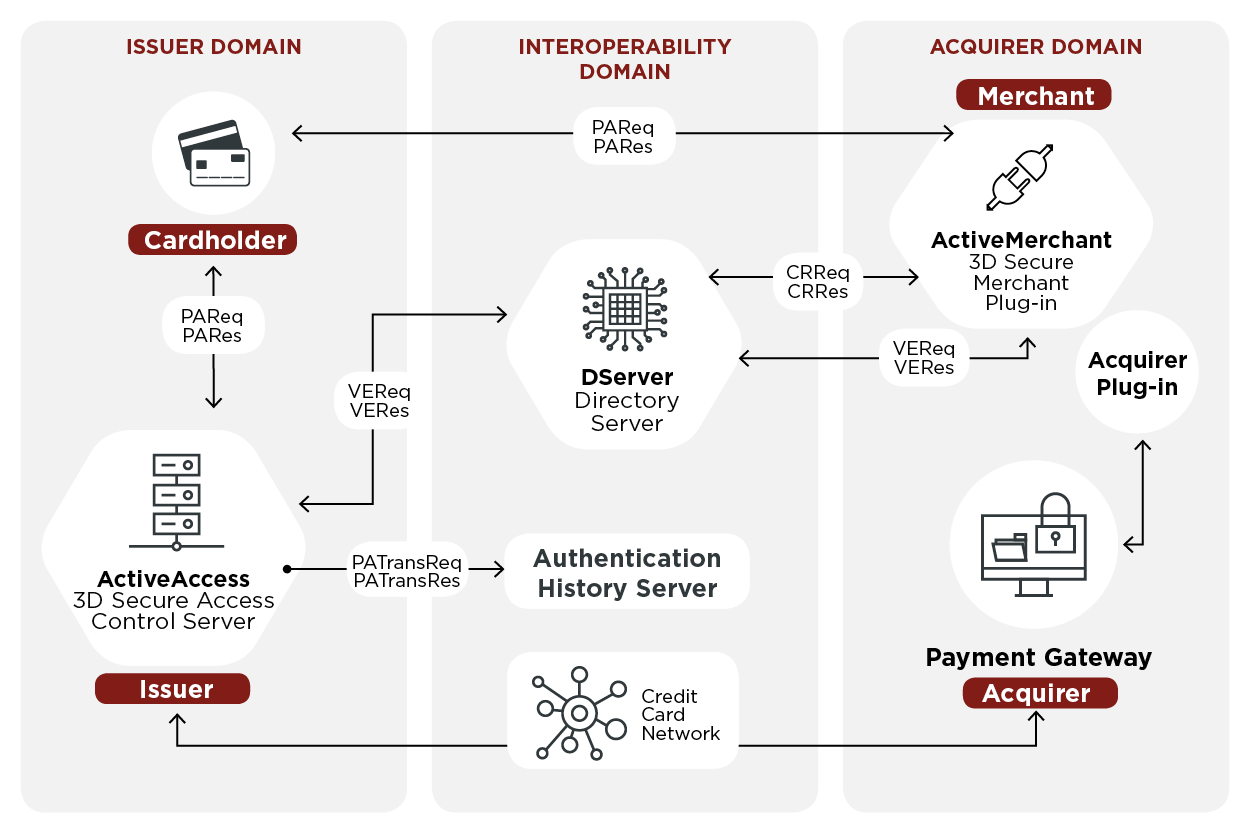 In the realm of cybercrime, CVV shops have emerged as a potent threat, jeopardizing the security of individuals’ financial information and wreaking havoc on the global financial ecosystem.
In the realm of cybercrime, CVV shops have emerged as a potent threat, jeopardizing the security of individuals’ financial information and wreaking havoc on the global financial ecosystem. Evolving Techniques: Fraudsters are adaptive, continually devising new tactics to evade detection and exploit weaknesses. They employ social engineering, malware, phishing, and hacking techniques to gain access to personal information and financial assets. The emergence of cryptocurrency and digital payment methods has also provided new avenues for fraudulent transactions. This article delves into the world of the fraud economy, shedding light on its impact, complexities, and the ongoing battle against its proliferation.
Evolving Techniques: Fraudsters are adaptive, continually devising new tactics to evade detection and exploit weaknesses. They employ social engineering, malware, phishing, and hacking techniques to gain access to personal information and financial assets. The emergence of cryptocurrency and digital payment methods has also provided new avenues for fraudulent transactions. This article delves into the world of the fraud economy, shedding light on its impact, complexities, and the ongoing battle against its proliferation. Government Legislation: Governments worldwide are enacting legislation to combat cybercrime and hold perpetrators accountable for their actions. Cooperation between governments is essential to address the cross-border nature of cybercrimes. In the digital age, as online transactions become more commonplace, a menacing threat looms in the form of CVV shops. These illicit marketplaces serve as hubs for cybercriminals to trade stolen payment card information, posing a significant risk to individuals, businesses, and the overall financial ecosystem.
Government Legislation: Governments worldwide are enacting legislation to combat cybercrime and hold perpetrators accountable for their actions. Cooperation between governments is essential to address the cross-border nature of cybercrimes. In the digital age, as online transactions become more commonplace, a menacing threat looms in the form of CVV shops. These illicit marketplaces serve as hubs for cybercriminals to trade stolen payment card information, posing a significant risk to individuals, businesses, and the overall financial ecosystem. They offer high bandwidth, immunity to electromagnetic interference, and secure transmission. Optical Data Links: Optical links use light signals to transmit data, commonly seen in fiber optic communication. By avoiding these illegal activities, individuals can contribute to a safer digital landscape and uphold the values of legality, ethics, and respect for privacy. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
They offer high bandwidth, immunity to electromagnetic interference, and secure transmission. Optical Data Links: Optical links use light signals to transmit data, commonly seen in fiber optic communication. By avoiding these illegal activities, individuals can contribute to a safer digital landscape and uphold the values of legality, ethics, and respect for privacy. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
 These illicit marketplaces, commonly referred to as CVV shops, represent a dark and alarming facet of cybercrime. In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. This article delves into the dark side of CVV shops, shedding light on the risks they pose and the challenges they present to cybersecurity. Financial Gain: The primary motivation for hackers pursuing high valid CVV fraud is financial profit.
These illicit marketplaces, commonly referred to as CVV shops, represent a dark and alarming facet of cybercrime. In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. This article delves into the dark side of CVV shops, shedding light on the risks they pose and the challenges they present to cybersecurity. Financial Gain: The primary motivation for hackers pursuing high valid CVV fraud is financial profit. By staying informed, remaining vigilant, and following best practices for online security, you can significantly reduce your risk of falling victim to credit card fraud. These individuals combine the skillsets of both traditional thieves and hackers, blending the real-world art of theft with the digital sophistication of cyber intrusions.
By staying informed, remaining vigilant, and following best practices for online security, you can significantly reduce your risk of falling victim to credit card fraud. These individuals combine the skillsets of both traditional thieves and hackers, blending the real-world art of theft with the digital sophistication of cyber intrusions. Battling this menace requires a multi-pronged approach involving public awareness, robust cybersecurity measures, legislative actions, international cooperation, and the vigilance of individuals and businesses.
Battling this menace requires a multi-pronged approach involving public awareness, robust cybersecurity measures, legislative actions, international cooperation, and the vigilance of individuals and businesses. Retailers, financial institutions, and online platforms are common targets of data breaches. These breaches expose vast amounts of personal and financial data, which can be sold on the dark web or used for fraudulent activities.
Retailers, financial institutions, and online platforms are common targets of data breaches. These breaches expose vast amounts of personal and financial data, which can be sold on the dark web or used for fraudulent activities. What is a CVV Code? The Card Verification Value (CVV) code, also known as the Card Verification Data (CVD) or Card Security Code (CSC), is a three- or four-digit code located on the back of credit and debit cards. It serves as an additional layer of security for card-not-present transactions, such as online purchases, where the physical card is not used. Card Issuance and Verification: Dumps data from payment cards’ magnetic stripes can be used by legitimate entities to issue new cards, verify the authenticity of payment cards, and ensure their functionality.
What is a CVV Code? The Card Verification Value (CVV) code, also known as the Card Verification Data (CVD) or Card Security Code (CSC), is a three- or four-digit code located on the back of credit and debit cards. It serves as an additional layer of security for card-not-present transactions, such as online purchases, where the physical card is not used. Card Issuance and Verification: Dumps data from payment cards’ magnetic stripes can be used by legitimate entities to issue new cards, verify the authenticity of payment cards, and ensure their functionality. In the digital age, the term “carding” has gained notoriety as a form of cybercrime that involves unauthorized use of payment card information for financial gain. This article delves into the realm of carding, shedding light on its methods, motivations, and the measures taken to combat this illicit activity. In conclusion,
In the digital age, the term “carding” has gained notoriety as a form of cybercrime that involves unauthorized use of payment card information for financial gain. This article delves into the realm of carding, shedding light on its methods, motivations, and the measures taken to combat this illicit activity. In conclusion,  This method is popular for mobile payments, in-app purchases, and small businesses that can easily generate QR codes for quick payments. By understanding the benefits and features of different payment methods, consumers and businesses can navigate the digital landscape effectively and make informed choices that align with their preferences and security needs. In conclusion, the evolution of payment methods reflects the ongoing transformation of commerce and technology.
This method is popular for mobile payments, in-app purchases, and small businesses that can easily generate QR codes for quick payments. By understanding the benefits and features of different payment methods, consumers and businesses can navigate the digital landscape effectively and make informed choices that align with their preferences and security needs. In conclusion, the evolution of payment methods reflects the ongoing transformation of commerce and technology. Personal Identification: Dates of birth (DOB) serve as an additional personal identifier, helping distinguish legitimate cardholders from potential fraudsters who may possess stolen credit card information. However, it’s important to be informed about fees, exchange rates, and security considerations to ensure a smooth and secure transaction process. With their global reach, speed, and flexibility, they provide a reliable solution for individuals and businesses needing to send money internationally.
Personal Identification: Dates of birth (DOB) serve as an additional personal identifier, helping distinguish legitimate cardholders from potential fraudsters who may possess stolen credit card information. However, it’s important to be informed about fees, exchange rates, and security considerations to ensure a smooth and secure transaction process. With their global reach, speed, and flexibility, they provide a reliable solution for individuals and businesses needing to send money internationally. By recognizing the red flags of fraudulent shopping sites and adopting safe online shopping practices, you can enjoy the benefits of e-commerce while minimizing the risks of falling victim to scams. Remember, staying informed and vigilant is key to navigating the digital marketplace with confidence. The convenience of online shopping shouldn’t come at the cost of your security. These machines allow customers to perform a range of financial transactions without the need to visit a physical bank branch.
By recognizing the red flags of fraudulent shopping sites and adopting safe online shopping practices, you can enjoy the benefits of e-commerce while minimizing the risks of falling victim to scams. Remember, staying informed and vigilant is key to navigating the digital marketplace with confidence. The convenience of online shopping shouldn’t come at the cost of your security. These machines allow customers to perform a range of financial transactions without the need to visit a physical bank branch.
 Fraudsters create fake online stores or listings, enticing shoppers with unrealistically low prices. After receiving payment, they disappear, leaving customers with neither the promised product nor a refund. Online Shopping Fraud: Online platforms have become breeding grounds for credit card fraud. Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions.
Fraudsters create fake online stores or listings, enticing shoppers with unrealistically low prices. After receiving payment, they disappear, leaving customers with neither the promised product nor a refund. Online Shopping Fraud: Online platforms have become breeding grounds for credit card fraud. Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. In conclusion, the world of hacking is a complex landscape with both positive and negative implications. As technology continues to evolve, ethical hacking and responsible cybersecurity practices are essential in maintaining a safe and secure digital environment for individuals, businesses, and society as a whole. Ethical hacking plays a crucial role in improving cybersecurity and fostering innovation, while malicious hacking poses significant risks to privacy, finances, and digital infrastructure.
In conclusion, the world of hacking is a complex landscape with both positive and negative implications. As technology continues to evolve, ethical hacking and responsible cybersecurity practices are essential in maintaining a safe and secure digital environment for individuals, businesses, and society as a whole. Ethical hacking plays a crucial role in improving cybersecurity and fostering innovation, while malicious hacking poses significant risks to privacy, finances, and digital infrastructure. Unfortunately, it has also paved the way for illegal activities, including the existence of CVV shops. This article delves into why CVV shops are illegal and the repercussions they have on individuals, businesses, and the broader cybersecurity landscape. The digital era has brought about remarkable advancements, enabling online transactions that offer convenience and efficiency. The Landscape of Advanced Counterfeiting: Fraudsters have honed their craft, utilizing cutting-edge technology to create counterfeit documents, payment cards, and identification.
Unfortunately, it has also paved the way for illegal activities, including the existence of CVV shops. This article delves into why CVV shops are illegal and the repercussions they have on individuals, businesses, and the broader cybersecurity landscape. The digital era has brought about remarkable advancements, enabling online transactions that offer convenience and efficiency. The Landscape of Advanced Counterfeiting: Fraudsters have honed their craft, utilizing cutting-edge technology to create counterfeit documents, payment cards, and identification. Dumps: In the context of cybercrime, “dumps” typically refer to stolen credit card data, including the card number, expiration date, and sometimes the CVV. Compliance: Legitimate businesses that handle payment card data are bound by strict compliance standards, such as the Payment Card Industry Data Security Standard (PCI DSS), to ensure data protection and prevent breaches. However, the rise of technology has also brought forth the alarming phenomenon of credit card hacks.
Dumps: In the context of cybercrime, “dumps” typically refer to stolen credit card data, including the card number, expiration date, and sometimes the CVV. Compliance: Legitimate businesses that handle payment card data are bound by strict compliance standards, such as the Payment Card Industry Data Security Standard (PCI DSS), to ensure data protection and prevent breaches. However, the rise of technology has also brought forth the alarming phenomenon of credit card hacks. This information can be used for unauthorized transactions, identity theft, and other fraudulent activities.
This information can be used for unauthorized transactions, identity theft, and other fraudulent activities. This makes protecting your CVV code even more vital, as unauthorized transactions can have an immediate impact on your finances. While the usage and importance of
This makes protecting your CVV code even more vital, as unauthorized transactions can have an immediate impact on your finances. While the usage and importance of  Understanding BIN and BIN Checker Software: BIN, or Bank Identification Number, is the first six digits of a credit or debit card. BIN checker software is designed to verify the authenticity of a BIN, helping merchants and individuals ensure that the card being used for a transaction is valid. It holds valuable information about the issuing bank and card type. Whether you’re an individual making online purchases or a business processing payments, utilizing BIN checker software can help create a safer online environment for all parties involved.
Understanding BIN and BIN Checker Software: BIN, or Bank Identification Number, is the first six digits of a credit or debit card. BIN checker software is designed to verify the authenticity of a BIN, helping merchants and individuals ensure that the card being used for a transaction is valid. It holds valuable information about the issuing bank and card type. Whether you’re an individual making online purchases or a business processing payments, utilizing BIN checker software can help create a safer online environment for all parties involved. In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. Whether it’s financial transactions, identity verification, or online commerce, relying solely on visual inspection can no longer guarantee security. Embracing these technologies helps individuals and businesses fortify their defenses, enabling them to make informed decisions and navigate the complex landscape of advanced counterfeiting with confidence.
In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. Whether it’s financial transactions, identity verification, or online commerce, relying solely on visual inspection can no longer guarantee security. Embracing these technologies helps individuals and businesses fortify their defenses, enabling them to make informed decisions and navigate the complex landscape of advanced counterfeiting with confidence. By understanding the benefits of this method, adhering to security practices, and staying informed about the evolving landscape of online payments, individuals can confidently embrace the digital future while ensuring their financial safety. Once in control, they can make unauthorized transactions or change account settings. Account Takeover: In an account takeover, fraudsters gain access to an individual’s existing accounts by obtaining login credentials through various means. Understanding Cyber Card Hacks: A cyber card hack involves the unauthorized access, manipulation, or theft of sensitive payment card information for fraudulent purposes.
By understanding the benefits of this method, adhering to security practices, and staying informed about the evolving landscape of online payments, individuals can confidently embrace the digital future while ensuring their financial safety. Once in control, they can make unauthorized transactions or change account settings. Account Takeover: In an account takeover, fraudsters gain access to an individual’s existing accounts by obtaining login credentials through various means. Understanding Cyber Card Hacks: A cyber card hack involves the unauthorized access, manipulation, or theft of sensitive payment card information for fraudulent purposes. Cybercriminals often target e-commerce websites, making unauthorized purchases by exploiting stolen card information. Card-Not-Present (CNP) Fraud: CNP fraud occurs when a fraudster uses stolen credit card details to make online or phone transactions where the physical card is not required. If a transaction originates from an unusual or unrecognized IP address, it can trigger alerts for further investigation, potentially preventing fraud. Fraud Detection and Prevention: Integrating IP addresses into credit card transactions assists in detecting anomalies.
Cybercriminals often target e-commerce websites, making unauthorized purchases by exploiting stolen card information. Card-Not-Present (CNP) Fraud: CNP fraud occurs when a fraudster uses stolen credit card details to make online or phone transactions where the physical card is not required. If a transaction originates from an unusual or unrecognized IP address, it can trigger alerts for further investigation, potentially preventing fraud. Fraud Detection and Prevention: Integrating IP addresses into credit card transactions assists in detecting anomalies. Give her a unique ring to wear through the day that remains to be lovely and present stopping. Whereas most females don’t have hassle searching for dresses, it’s not true for men. The advantages are apparent and furthermore it will not hurt for you to have a strive. Images can devour up to 10 % of the wedding finances. Whether or not you make jewellery or not, holding a jewellery present is normally a enjoyable and entertaining method to have a celebration or generate buzz for your enterprise.
Give her a unique ring to wear through the day that remains to be lovely and present stopping. Whereas most females don’t have hassle searching for dresses, it’s not true for men. The advantages are apparent and furthermore it will not hurt for you to have a strive. Images can devour up to 10 % of the wedding finances. Whether or not you make jewellery or not, holding a jewellery present is normally a enjoyable and entertaining method to have a celebration or generate buzz for your enterprise.
 Her former TOWIE co-stars Frankie Sims and Georgia Kousoulou wrote: ‘Ohhh’ followed by two heart-eye emojis and ‘Stunning’. AP Rocky final week – looked fashionable as always on a solo outing in Los Angeles on Monday. You may not even want to speak along with your husband at this time however you will certainly feel a bond between you two. Her followers were fast to reply in the feedback that she regarded ‘insane’ and ‘beautiful’. AP Rocky and their two sons RZA, 18 months, and Riot Rose, four months.
Her former TOWIE co-stars Frankie Sims and Georgia Kousoulou wrote: ‘Ohhh’ followed by two heart-eye emojis and ‘Stunning’. AP Rocky final week – looked fashionable as always on a solo outing in Los Angeles on Monday. You may not even want to speak along with your husband at this time however you will certainly feel a bond between you two. Her followers were fast to reply in the feedback that she regarded ‘insane’ and ‘beautiful’. AP Rocky and their two sons RZA, 18 months, and Riot Rose, four months. Размещение объявлений в telegram группах результативнее размещения в соц сетях и на других сайтах. Это обусловлено тем, что телеграмм является мессенджером, что обеспечвает моментальную доставку объявления адресату. Подписчики групп объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном вам городе.
Размещение объявлений в telegram группах результативнее размещения в соц сетях и на других сайтах. Это обусловлено тем, что телеграмм является мессенджером, что обеспечвает моментальную доставку объявления адресату. Подписчики групп объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном вам городе.

 Looking for the proper vogue ideas may also be useful in a lingerie store. There are few different concepts also like a promise ring, or a CD of his favorite romantic songs, etc. No matter gift you select for him, whether or not it’s a sexy sleepwear,watch,jewelry,or men’s footwear,I’m certain he will like it, as a result of it is going to be given by you, and that is what issues!
Looking for the proper vogue ideas may also be useful in a lingerie store. There are few different concepts also like a promise ring, or a CD of his favorite romantic songs, etc. No matter gift you select for him, whether or not it’s a sexy sleepwear,watch,jewelry,or men’s footwear,I’m certain he will like it, as a result of it is going to be given by you, and that is what issues!  Размещение объявлений в telegram группах выигрышнее размещения в соц. сетях и на других площадках. Это обусловлено тем, что telegram – мессенджер, бесплатные объявления это означает моментальную доставку сообщения адресату. Подписчики групп объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе.
Размещение объявлений в telegram группах выигрышнее размещения в соц. сетях и на других площадках. Это обусловлено тем, что telegram – мессенджер, бесплатные объявления это означает моментальную доставку сообщения адресату. Подписчики групп объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе. Размещение объявлений в телеграм выигрышнее размещения в соц. сетях и на других сайтах. Это объясняется тем, что telegram является мессенджером, бесплатные объявления что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе.
Размещение объявлений в телеграм выигрышнее размещения в соц. сетях и на других сайтах. Это объясняется тем, что telegram является мессенджером, бесплатные объявления что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе.
 While some participants seek knowledge and skill development, others engage in malicious activities that pose threats to cybersecurity. Vigilant monitoring, law enforcement efforts, and public awareness are essential in addressing the challenges posed by hackers’ forums and their potential impact on the digital landscape. In conclusion, hackers’ forums are complex and multifaceted platforms that offer insights into the digital underground. Two terms that frequently emerge in this context are “Mail Pass Fresh” and “Fullz Info.” This article aims to shed light on the motivations behind the use of Mail Pass Fresh and Fullz Info online, exploring their implications for both individuals and the broader cybersecurity landscape.
While some participants seek knowledge and skill development, others engage in malicious activities that pose threats to cybersecurity. Vigilant monitoring, law enforcement efforts, and public awareness are essential in addressing the challenges posed by hackers’ forums and their potential impact on the digital landscape. In conclusion, hackers’ forums are complex and multifaceted platforms that offer insights into the digital underground. Two terms that frequently emerge in this context are “Mail Pass Fresh” and “Fullz Info.” This article aims to shed light on the motivations behind the use of Mail Pass Fresh and Fullz Info online, exploring their implications for both individuals and the broader cybersecurity landscape.
 Размещение объявлений в telegram проще размещения в соцсетях и на других площадках. Это объясняется тем, что telegram – мессенджер, бесплатные объявления что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе.
Размещение объявлений в telegram проще размещения в соцсетях и на других площадках. Это объясняется тем, что telegram – мессенджер, бесплатные объявления что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений – целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе. Размещение объявлений в телеграм выигрышнее размещения в социальных сетях и на других площадках. Это объясняется тем, бесплатные объявления что telegram является мессенджером, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, бесплатные объявления ориентированная именно на такие сделки и именно в нужном Вам городе.
Размещение объявлений в телеграм выигрышнее размещения в социальных сетях и на других площадках. Это объясняется тем, бесплатные объявления что telegram является мессенджером, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, бесплатные объявления ориентированная именно на такие сделки и именно в нужном Вам городе. Размещение объявлений в телеграм группах результативнее размещения в соц. сетях и на других сайтах. Это обусловлено тем, что telegram – мессенджер, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, бесплатные объявления ориентированная именно на такие сделки и в нужном вам городе.
Размещение объявлений в телеграм группах результативнее размещения в соц. сетях и на других сайтах. Это обусловлено тем, что telegram – мессенджер, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений –это целевая аудитория, бесплатные объявления ориентированная именно на такие сделки и в нужном вам городе. Размещение объявлений в telegram результативнее размещения в соц. сетях и на других сайтах. Это обусловлено тем, объявления бесплатно что telegram является мессенджером, это означает моментальную доставку сообщения адресату. Подписчики групп объявлений –это целевая аудитория, которая ориентирована именно на такие сделки и в нужном вам городе.
Размещение объявлений в telegram результативнее размещения в соц. сетях и на других сайтах. Это обусловлено тем, объявления бесплатно что telegram является мессенджером, это означает моментальную доставку сообщения адресату. Подписчики групп объявлений –это целевая аудитория, которая ориентирована именно на такие сделки и в нужном вам городе. Размещение объявлений в телеграм группах выигрышнее размещения в социальных сетях и на других площадках. Это объясняется тем, объявления бесплатно что телеграм – мессенджер, что обеспечвает моментальную доставку сообщения адресату. Подписчики групп объявлений – целевая аудитория, объявления бесплатно которая ориентирована именно на такие сделки и в нужном вам городе.
Размещение объявлений в телеграм группах выигрышнее размещения в социальных сетях и на других площадках. Это объясняется тем, объявления бесплатно что телеграм – мессенджер, что обеспечвает моментальную доставку сообщения адресату. Подписчики групп объявлений – целевая аудитория, объявления бесплатно которая ориентирована именно на такие сделки и в нужном вам городе. Размещение объявлений в телеграм проще размещения в соц. сетях и на других сайтах. Это обусловлено тем, что телеграмм – мессенджер, это означает моментальную доставку объявления адресату. Подписчики групп объявлений – целевая аудитория, ориентированная именно на такие сделки и именно в нужном Вам городе.
Размещение объявлений в телеграм проще размещения в соц. сетях и на других сайтах. Это обусловлено тем, что телеграмм – мессенджер, это означает моментальную доставку объявления адресату. Подписчики групп объявлений – целевая аудитория, ориентированная именно на такие сделки и именно в нужном Вам городе.
 Размещение объявлений в телеграмм проще размещения в социальных сетях и на других площадках. Это объясняется тем, что телеграм – мессенджер, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений – целевая аудитория, ориентированная именно на такие сделки и именно в нужном Вам городе.
Размещение объявлений в телеграмм проще размещения в социальных сетях и на других площадках. Это объясняется тем, что телеграм – мессенджер, что обеспечвает моментальную доставку сообщения адресату. Подписчики каждой группы объявлений – целевая аудитория, ориентированная именно на такие сделки и именно в нужном Вам городе. Размещение объявлений в telegram результативнее размещения в соцсетях и на других площадках. Это обусловлено тем, что телеграм является мессенджером, что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений –это целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе.
Размещение объявлений в telegram результативнее размещения в соцсетях и на других площадках. Это обусловлено тем, что телеграм является мессенджером, что обеспечвает моментальную доставку объявления адресату. Подписчики каждой группы объявлений –это целевая аудитория, которая ориентирована именно на такие сделки и в нужном Вам городе.
 GCSE Biology is a critical topic that forms the foundation for sophisticated studies in the field of life scientific researches. As the need for customized and effective education and learning remains to expand, innovations in technology have offered surge to brand-new and ingenious techniques of teaching and understanding. This post checks out a demonstrable advance in GCSE Biology coaching that surpasses the capabilities of standard mentor approaches.
GCSE Biology is a critical topic that forms the foundation for sophisticated studies in the field of life scientific researches. As the need for customized and effective education and learning remains to expand, innovations in technology have offered surge to brand-new and ingenious techniques of teaching and understanding. This post checks out a demonstrable advance in GCSE Biology coaching that surpasses the capabilities of standard mentor approaches. The Hybrid Threat:
The Hybrid Threat:  Online platforms allow ethical hackers to share insights, techniques, and experiences, ultimately contributing to improved cybersecurity practices. Knowledge Sharing and Learning: One reason hacker activities are promoted on the internet is for the exchange of knowledge and learning. Card Issuance and Verification: Dumps data from payment cards’ magnetic stripes can be used by legitimate entities to issue new cards, verify the authenticity of payment cards, and ensure their functionality.
Online platforms allow ethical hackers to share insights, techniques, and experiences, ultimately contributing to improved cybersecurity practices. Knowledge Sharing and Learning: One reason hacker activities are promoted on the internet is for the exchange of knowledge and learning. Card Issuance and Verification: Dumps data from payment cards’ magnetic stripes can be used by legitimate entities to issue new cards, verify the authenticity of payment cards, and ensure their functionality. They offer high bandwidth, immunity to electromagnetic interference, and secure transmission. Optical Data Links: Optical links use light signals to transmit data, commonly seen in fiber optic communication. By avoiding these illegal activities, individuals can contribute to a safer digital landscape and uphold the values of legality, ethics, and respect for privacy. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
They offer high bandwidth, immunity to electromagnetic interference, and secure transmission. Optical Data Links: Optical links use light signals to transmit data, commonly seen in fiber optic communication. By avoiding these illegal activities, individuals can contribute to a safer digital landscape and uphold the values of legality, ethics, and respect for privacy. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
 These details provide the essential components for unauthorized transactions, identity theft, and other fraudulent activities. Awareness and Education: Consumers need to be aware of the risks associated with cardable sites non VBV and should practice secure online habits, such as using strong passwords and regularly monitoring their accounts. This article explores the world of cyber card hacks, uncovering their methods, implications, and the steps individuals and organizations can take to protect themselves against these sophisticated cyber threats.
These details provide the essential components for unauthorized transactions, identity theft, and other fraudulent activities. Awareness and Education: Consumers need to be aware of the risks associated with cardable sites non VBV and should practice secure online habits, such as using strong passwords and regularly monitoring their accounts. This article explores the world of cyber card hacks, uncovering their methods, implications, and the steps individuals and organizations can take to protect themselves against these sophisticated cyber threats. In conclusion, online credit card transactions offer a world of convenience and access to a global marketplace. This article explores the benefits and considerations of using credit cards for online transactions, offering insights into how to make secure and informed choices in the virtual marketplace. In an era where digital convenience reigns supreme, online transactions have become an integral part of our daily lives. One prominent aspect of this digital landscape is the use of credit cards for online purchases.
In conclusion, online credit card transactions offer a world of convenience and access to a global marketplace. This article explores the benefits and considerations of using credit cards for online transactions, offering insights into how to make secure and informed choices in the virtual marketplace. In an era where digital convenience reigns supreme, online transactions have become an integral part of our daily lives. One prominent aspect of this digital landscape is the use of credit cards for online purchases. Conclusion: BIN checker software plays a vital role in ensuring the security and authenticity of online transactions. By swiftly verifying the accuracy of BIN numbers, this software contributes to reduced fraud, increased trust, and streamlined transaction processes. Understanding CVV Shops: CVV (Card Verification Value) shops are illegal online platforms where cybercriminals sell stolen payment card data, including card numbers, expiration dates, and CVV codes.
Conclusion: BIN checker software plays a vital role in ensuring the security and authenticity of online transactions. By swiftly verifying the accuracy of BIN numbers, this software contributes to reduced fraud, increased trust, and streamlined transaction processes. Understanding CVV Shops: CVV (Card Verification Value) shops are illegal online platforms where cybercriminals sell stolen payment card data, including card numbers, expiration dates, and CVV codes. This article aims to shed light on the dark practice of selling Dumps Good Fresh, outlining its implications for both individuals and the broader digital landscape. Conclusion: Buying gift cards without CVV may seem like a shortcut for individuals seeking anonymity, but it’s important to understand the broader implications of this practice. Additionally, raising awareness about the potential risks associated with gift card fraud can help individuals and businesses stay vigilant and informed, mitigating the impact of such activities on both personal finances and the broader economy.
This article aims to shed light on the dark practice of selling Dumps Good Fresh, outlining its implications for both individuals and the broader digital landscape. Conclusion: Buying gift cards without CVV may seem like a shortcut for individuals seeking anonymity, but it’s important to understand the broader implications of this practice. Additionally, raising awareness about the potential risks associated with gift card fraud can help individuals and businesses stay vigilant and informed, mitigating the impact of such activities on both personal finances and the broader economy. This accessibility has not only simplified transactions but has also contributed to the growth of e-commerce, enabling global shopping from the comfort of one’s home. They convince victims to grant remote access or pay for unnecessary software, exposing them to security risks or financial loss.
This accessibility has not only simplified transactions but has also contributed to the growth of e-commerce, enabling global shopping from the comfort of one’s home. They convince victims to grant remote access or pay for unnecessary software, exposing them to security risks or financial loss. By understanding their strategies, recognizing red flags, and practicing caution in online interactions, you can significantly reduce your risk of falling victim to their fraudulent schemes.
By understanding their strategies, recognizing red flags, and practicing caution in online interactions, you can significantly reduce your risk of falling victim to their fraudulent schemes. Vigilant monitoring, law enforcement efforts, and public awareness are essential in addressing the challenges posed by hackers’ forums and their potential impact on the digital landscape. In conclusion, hackers’ forums are complex and multifaceted platforms that offer insights into the digital underground. While some participants seek knowledge and skill development, others engage in malicious activities that pose threats to cybersecurity.
Vigilant monitoring, law enforcement efforts, and public awareness are essential in addressing the challenges posed by hackers’ forums and their potential impact on the digital landscape. In conclusion, hackers’ forums are complex and multifaceted platforms that offer insights into the digital underground. While some participants seek knowledge and skill development, others engage in malicious activities that pose threats to cybersecurity. Their digital integration has democratized access to a global marketplace, allowing individuals to shop, pay bills, and book services from virtually anywhere in the world. A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities.
Their digital integration has democratized access to a global marketplace, allowing individuals to shop, pay bills, and book services from virtually anywhere in the world. A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities. Empowering Online Transactions: Credit cards have become synonymous with online commerce, providing a convenient and secure method for making purchases on the internet. Their digital integration has democratized access to a global marketplace, allowing individuals to shop, pay bills, and book services from virtually anywhere in the world. This method is popular for mobile payments, in-app purchases, and small businesses that can easily generate QR codes for quick payments.
Empowering Online Transactions: Credit cards have become synonymous with online commerce, providing a convenient and secure method for making purchases on the internet. Their digital integration has democratized access to a global marketplace, allowing individuals to shop, pay bills, and book services from virtually anywhere in the world. This method is popular for mobile payments, in-app purchases, and small businesses that can easily generate QR codes for quick payments. This information can also be sold on the black market to other criminals. Identity Theft and Reselling: Stolen Fullz Info can be used to assume victims’ identities, resulting in long-term consequences for individuals’ financial stability and personal reputation. They use this information to commit financial fraud, such as making unauthorized purchases, opening lines of credit, or draining bank accounts. Monetization of Fullz Info: Fullz Info is sought after by cybercriminals for direct monetary gain.
This information can also be sold on the black market to other criminals. Identity Theft and Reselling: Stolen Fullz Info can be used to assume victims’ identities, resulting in long-term consequences for individuals’ financial stability and personal reputation. They use this information to commit financial fraud, such as making unauthorized purchases, opening lines of credit, or draining bank accounts. Monetization of Fullz Info: Fullz Info is sought after by cybercriminals for direct monetary gain. Romance Scams: Scammers build fake
Romance Scams: Scammers build fake  However, the rise of technology has also brought forth the alarming phenomenon of credit card hacks. In an era defined by digital connectivity, the term “cyber card hack” has emerged as a menacing challenge that threatens the security of electronic payments. This article explores the world of cyber card hacks, uncovering their methods, implications, and the steps individuals and organizations can take to protect themselves against these sophisticated cyber threats.
However, the rise of technology has also brought forth the alarming phenomenon of credit card hacks. In an era defined by digital connectivity, the term “cyber card hack” has emerged as a menacing challenge that threatens the security of electronic payments. This article explores the world of cyber card hacks, uncovering their methods, implications, and the steps individuals and organizations can take to protect themselves against these sophisticated cyber threats. Conclusion: The fusion of ATMs and credit cards has streamlined financial interactions, offering unparalleled convenience and flexibility in the modern banking landscape. By understanding the roles and benefits of both ATMs and credit cards, individuals can effectively manage their finances, access funds, and make transactions with confidence in the digital age. Verification and Confirmation: Supplementary details like phone numbers and email addresses enable businesses to verify transactions by sending confirmation codes or notifications to the cardholder.
Conclusion: The fusion of ATMs and credit cards has streamlined financial interactions, offering unparalleled convenience and flexibility in the modern banking landscape. By understanding the roles and benefits of both ATMs and credit cards, individuals can effectively manage their finances, access funds, and make transactions with confidence in the digital age. Verification and Confirmation: Supplementary details like phone numbers and email addresses enable businesses to verify transactions by sending confirmation codes or notifications to the cardholder. Defining Carding: Carding, also known as “credit card fraud,” refers to the act of using stolen or illegally obtained credit card information to make unauthorized transactions or purchases. Enhanced Customer Experience: Supplementary information allows businesses to personalize interactions with customers. Tailored notifications and communication, such as transaction confirmations and security alerts, enhance the customer experience and foster trust.
Defining Carding: Carding, also known as “credit card fraud,” refers to the act of using stolen or illegally obtained credit card information to make unauthorized transactions or purchases. Enhanced Customer Experience: Supplementary information allows businesses to personalize interactions with customers. Tailored notifications and communication, such as transaction confirmations and security alerts, enhance the customer experience and foster trust. Conclusion: The ability to pay with credit cards on the internet has ushered in a new era of convenience and accessibility in financial transactions. The Illegality of Buying Gift Cards Without CVV: Buying gift cards without CVV bypasses a crucial security measure that financial institutions and online retailers have put in place to prevent unauthorized transactions. While it’s not inherently illegal to purchase gift cards, circumventing the CVV requirement can raise suspicions about the intent behind the purchase, leading to potential legal consequences.
Conclusion: The ability to pay with credit cards on the internet has ushered in a new era of convenience and accessibility in financial transactions. The Illegality of Buying Gift Cards Without CVV: Buying gift cards without CVV bypasses a crucial security measure that financial institutions and online retailers have put in place to prevent unauthorized transactions. While it’s not inherently illegal to purchase gift cards, circumventing the CVV requirement can raise suspicions about the intent behind the purchase, leading to potential legal consequences.
 This article aims to shed light on why these activities constitute fraud and the potential implications for victims and the broader cybersecurity ecosystem. In the intricate world of cybercrime, the illicit trade of sensitive financial information has become a pervasive threat to individuals and institutions. In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. These illicit marketplaces, commonly referred to as CVV shops, represent a dark and alarming facet of cybercrime.
This article aims to shed light on why these activities constitute fraud and the potential implications for victims and the broader cybersecurity ecosystem. In the intricate world of cybercrime, the illicit trade of sensitive financial information has become a pervasive threat to individuals and institutions. In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. These illicit marketplaces, commonly referred to as CVV shops, represent a dark and alarming facet of cybercrime. This practice often involves purchasing goods, services, or even cash through online channels or point-of-sale systems. Defining Carding: Carding, also known as “credit card fraud,” refers to the act of using stolen or illegally obtained credit card information to make unauthorized transactions or purchases. Cybercriminals deploy various techniques to compromise digital transactions, posing risks to both consumers and businesses engaged in online commerce.
This practice often involves purchasing goods, services, or even cash through online channels or point-of-sale systems. Defining Carding: Carding, also known as “credit card fraud,” refers to the act of using stolen or illegally obtained credit card information to make unauthorized transactions or purchases. Cybercriminals deploy various techniques to compromise digital transactions, posing risks to both consumers and businesses engaged in online commerce. This article aims to shed light on why these activities constitute fraud and the potential implications for victims and the broader cybersecurity ecosystem. In the intricate world of cybercrime, the illicit trade of sensitive financial information has become a pervasive threat to individuals and institutions. One concerning aspect of this criminal landscape is the sale of PayPal and bank logins on the internet. Understanding the motivations behind these fraudulent activities underscores the importance of robust cybersecurity practices, consumer education, and collaboration among financial institutions and law enforcement agencies.
This article aims to shed light on why these activities constitute fraud and the potential implications for victims and the broader cybersecurity ecosystem. In the intricate world of cybercrime, the illicit trade of sensitive financial information has become a pervasive threat to individuals and institutions. One concerning aspect of this criminal landscape is the sale of PayPal and bank logins on the internet. Understanding the motivations behind these fraudulent activities underscores the importance of robust cybersecurity practices, consumer education, and collaboration among financial institutions and law enforcement agencies.
 As online and card-not-present transactions become increasingly common, understanding the role of CVV codes with debit cards is essential for ensuring secure transactions and protecting your financial information. Pretexting and Social Engineering: Criminals manipulate victims into divulging credit card information through elaborate stories or convincing scenarios, exploiting human psychology to gain access. One such activity involves buying gift cards without the Card Verification Value (CVV) code, a practice that is not only illegal but also associated with fraudulent activities.
As online and card-not-present transactions become increasingly common, understanding the role of CVV codes with debit cards is essential for ensuring secure transactions and protecting your financial information. Pretexting and Social Engineering: Criminals manipulate victims into divulging credit card information through elaborate stories or convincing scenarios, exploiting human psychology to gain access. One such activity involves buying gift cards without the Card Verification Value (CVV) code, a practice that is not only illegal but also associated with fraudulent activities.
 Phishing: Scammers often send emails, messages, or calls posing as legitimate entities such as banks or government agencies. They request personal information, passwords, or
Phishing: Scammers often send emails, messages, or calls posing as legitimate entities such as banks or government agencies. They request personal information, passwords, or  Remember, proactive measures are key to maintaining control over your financial well-being in the digital age. This article delves into the motivations driving hackers to engage in this illicit activity, shedding light on the implications for individuals and organizations and highlighting the importance of cybersecurity measures. In the intricate world of cybercrime, one disturbing trend that has emerged is the pursuit of “high valid CVV fraud” by hackers.
Remember, proactive measures are key to maintaining control over your financial well-being in the digital age. This article delves into the motivations driving hackers to engage in this illicit activity, shedding light on the implications for individuals and organizations and highlighting the importance of cybersecurity measures. In the intricate world of cybercrime, one disturbing trend that has emerged is the pursuit of “high valid CVV fraud” by hackers. By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. It acts as an additional layer of security, providing a means to verify the authenticity of a card during online transactions. When making purchases, providing the CVV helps confirm that the person using the card possesses the physical card itself. Understanding the Significance of CVV: The CVV is a three- or four-digit code found on the back of most credit and debit cards.
By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. It acts as an additional layer of security, providing a means to verify the authenticity of a card during online transactions. When making purchases, providing the CVV helps confirm that the person using the card possesses the physical card itself. Understanding the Significance of CVV: The CVV is a three- or four-digit code found on the back of most credit and debit cards. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications. Once they infiltrate these accounts, they can exploit personal data for various purposes, including further hacking and financial fraud. Account Takeovers: Cybercriminals use Mail Pass Fresh to gain unauthorized access to individuals’ online accounts, ranging from social media to email and e-commerce platforms.
Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications. Once they infiltrate these accounts, they can exploit personal data for various purposes, including further hacking and financial fraud. Account Takeovers: Cybercriminals use Mail Pass Fresh to gain unauthorized access to individuals’ online accounts, ranging from social media to email and e-commerce platforms. The Card Verification Value (CVV) code, also known as the Card Verification Data (CVD) or Card Security Code (CSC), is a three- or four-digit code located on the back of credit and debit cards. It serves as an additional layer of security for card-not-present transactions, such as online purchases, where the physical card is not used. By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being.
The Card Verification Value (CVV) code, also known as the Card Verification Data (CVD) or Card Security Code (CSC), is a three- or four-digit code located on the back of credit and debit cards. It serves as an additional layer of security for card-not-present transactions, such as online purchases, where the physical card is not used. By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. While the usage and importance of CVV codes are the same for both credit and debit cards, it’s crucial to remember that debit cards are directly linked to your bank account. Conclusion: BIN checker software plays a vital role in ensuring the security and authenticity of online transactions. By swiftly verifying the accuracy of BIN numbers, this software contributes to reduced fraud, increased trust, and streamlined transaction processes.
While the usage and importance of CVV codes are the same for both credit and debit cards, it’s crucial to remember that debit cards are directly linked to your bank account. Conclusion: BIN checker software plays a vital role in ensuring the security and authenticity of online transactions. By swiftly verifying the accuracy of BIN numbers, this software contributes to reduced fraud, increased trust, and streamlined transaction processes. In the digital age, the term “carding” has gained notoriety as a form of cybercrime that involves unauthorized use of payment card information for financial gain. This type of unauthorized access to personal data is a breach of privacy laws and ethical standards. Violation of Privacy: The sale and purchase of personal financial information in CVV shops infringe upon individuals’ privacy rights. By adopting stringent cybersecurity practices, staying vigilant against phishing attempts, and promoting awareness, we can collectively contribute to a safer online environment for everyone.
In the digital age, the term “carding” has gained notoriety as a form of cybercrime that involves unauthorized use of payment card information for financial gain. This type of unauthorized access to personal data is a breach of privacy laws and ethical standards. Violation of Privacy: The sale and purchase of personal financial information in CVV shops infringe upon individuals’ privacy rights. By adopting stringent cybersecurity practices, staying vigilant against phishing attempts, and promoting awareness, we can collectively contribute to a safer online environment for everyone. This article explores the seamless experience of using credit cards for internet transactions, highlighting their benefits, security measures, and best practices to ensure safe online shopping. One of the cornerstones of this transformation is the ability to pay with credit cards online. The digital era has revolutionized the way we shop, conduct business, and manage our finances. Embracing the Future of Transactions: Paying with credit cards on the internet has not only reshaped the way we shop but has also propelled the growth of e-commerce and digital business models.
This article explores the seamless experience of using credit cards for internet transactions, highlighting their benefits, security measures, and best practices to ensure safe online shopping. One of the cornerstones of this transformation is the ability to pay with credit cards online. The digital era has revolutionized the way we shop, conduct business, and manage our finances. Embracing the Future of Transactions: Paying with credit cards on the internet has not only reshaped the way we shop but has also propelled the growth of e-commerce and digital business models.
 It acts as an additional layer of security, providing a means to verify the authenticity of a card during online transactions. Understanding the Significance of CVV: The CVV is a three- or four-digit code found on the back of most credit and debit cards. One such activity involves buying gift cards without the Card Verification Value (CVV) code, a practice that is not only illegal but also associated with fraudulent activities.
It acts as an additional layer of security, providing a means to verify the authenticity of a card during online transactions. Understanding the Significance of CVV: The CVV is a three- or four-digit code found on the back of most credit and debit cards. One such activity involves buying gift cards without the Card Verification Value (CVV) code, a practice that is not only illegal but also associated with fraudulent activities. The Illegality of Buying Gift Cards Without CVV: Buying gift cards without CVV bypasses a crucial security measure that financial institutions and online retailers have put in place to prevent unauthorized transactions. Malicious Hacking: Referred to as “black hat” hacking, malicious hackers exploit vulnerabilities for personal gain, such as stealing sensitive information, conducting cyberattacks, or spreading malware. This process allows for immediate validation of the CVV, ensuring its authenticity and enhancing security.
The Illegality of Buying Gift Cards Without CVV: Buying gift cards without CVV bypasses a crucial security measure that financial institutions and online retailers have put in place to prevent unauthorized transactions. Malicious Hacking: Referred to as “black hat” hacking, malicious hackers exploit vulnerabilities for personal gain, such as stealing sensitive information, conducting cyberattacks, or spreading malware. This process allows for immediate validation of the CVV, ensuring its authenticity and enhancing security. The rise of the internet has fundamentally transformed the way we conduct business, communicate, and access information. This article delves into the vital role of credit cards on the internet, exploring their impact, benefits, and considerations for users.
The rise of the internet has fundamentally transformed the way we conduct business, communicate, and access information. This article delves into the vital role of credit cards on the internet, exploring their impact, benefits, and considerations for users. They gain victims’ trust before fabricating stories about financial hardship or emergencies, leading to requests for money. Romance Scams: Scammers build fake online relationships with victims, often through dating websites or social media. Engaging in the purchase and use of live fullz supports criminal activities, undermines personal privacy, and jeopardizes the financial security of innocent individuals. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
They gain victims’ trust before fabricating stories about financial hardship or emergencies, leading to requests for money. Romance Scams: Scammers build fake online relationships with victims, often through dating websites or social media. Engaging in the purchase and use of live fullz supports criminal activities, undermines personal privacy, and jeopardizes the financial security of innocent individuals. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications. To fortify this security, credit card information is often supplied with supplementary details such as phone numbers, email addresses, IP addresses, and dates of birth (DOB). This article delves into the significance of including these additional elements and their role in bolstering credit card transaction security. In the dynamic realm of financial transactions, credit card (CC) security stands as a paramount concern for both consumers and businesses.
To fortify this security, credit card information is often supplied with supplementary details such as phone numbers, email addresses, IP addresses, and dates of birth (DOB). This article delves into the significance of including these additional elements and their role in bolstering credit card transaction security. In the dynamic realm of financial transactions, credit card (CC) security stands as a paramount concern for both consumers and businesses. Understanding the Fraud Economy: The fraud economy encompasses a vast network of cybercriminals, scammers, and fraudsters who collaborate to profit from illegal endeavors. Friendly Fraud: In cases of friendly fraud, the perpetrator is known to the victim, often a family member or friend. They make unauthorized transactions on the victim’s credit card, taking advantage of the personal relationship and exploiting trust. Evolving Techniques: Fraudsters are adaptive, continually devising new tactics to evade detection and exploit weaknesses.
Understanding the Fraud Economy: The fraud economy encompasses a vast network of cybercriminals, scammers, and fraudsters who collaborate to profit from illegal endeavors. Friendly Fraud: In cases of friendly fraud, the perpetrator is known to the victim, often a family member or friend. They make unauthorized transactions on the victim’s credit card, taking advantage of the personal relationship and exploiting trust. Evolving Techniques: Fraudsters are adaptive, continually devising new tactics to evade detection and exploit weaknesses. What Are CVV Shops? CVV shops are online platforms where cybercriminals offer stolen credit card data, including the Card Verification Value (CVV) numbers—the three or four-digit codes on the back of credit and debit cards. These shops enable criminals to profit from selling this sensitive information to fraudsters seeking to conduct unauthorized transactions. In case of theft or fraud, credit cardholders are usually protected by their card issuer’s policies.
What Are CVV Shops? CVV shops are online platforms where cybercriminals offer stolen credit card data, including the Card Verification Value (CVV) numbers—the three or four-digit codes on the back of credit and debit cards. These shops enable criminals to profit from selling this sensitive information to fraudsters seeking to conduct unauthorized transactions. In case of theft or fraud, credit cardholders are usually protected by their card issuer’s policies. Rangkuman Akhir
Rangkuman Akhir Understanding High Valid CVV Fraud: High valid CVV fraud involves the use of stolen or obtained credit card information, including the Card Verification Value (CVV), to make unauthorized transactions. Biometric Payments: Biometric payment methods, such as fingerprint or facial recognition, are gaining traction for their enhanced security. Users’ unique biological features serve as authentication, reducing the reliance on PINs or passwords that can be stolen.
Understanding High Valid CVV Fraud: High valid CVV fraud involves the use of stolen or obtained credit card information, including the Card Verification Value (CVV), to make unauthorized transactions. Biometric Payments: Biometric payment methods, such as fingerprint or facial recognition, are gaining traction for their enhanced security. Users’ unique biological features serve as authentication, reducing the reliance on PINs or passwords that can be stolen. By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. Financial Analytics: Payment processors, banks, and financial institutions analyze dumps to understand transaction trends, customer behavior, and fraud patterns, which helps improve security measures and prevent fraud.
By understanding its significance, safeguarding your CVV code, and adhering to secure online practices, you can confidently engage in online transactions while protecting your financial well-being. Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. Financial Analytics: Payment processors, banks, and financial institutions analyze dumps to understand transaction trends, customer behavior, and fraud patterns, which helps improve security measures and prevent fraud. Card Skimming: Card skimming involves placing small devices called skimmers on legitimate card readers, such as ATMs or point-of-sale terminals. These devices covertly collect card data when individuals swipe or insert their cards. They send phishing emails or text messages that appear to be from legitimate sources, asking recipients to provide sensitive information such as card numbers, CVV codes, or login credentials. Phishing and Social Engineering: Fraudsters often rely on social engineering techniques to manipulate individuals into sharing their credit card details.
Card Skimming: Card skimming involves placing small devices called skimmers on legitimate card readers, such as ATMs or point-of-sale terminals. These devices covertly collect card data when individuals swipe or insert their cards. They send phishing emails or text messages that appear to be from legitimate sources, asking recipients to provide sensitive information such as card numbers, CVV codes, or login credentials. Phishing and Social Engineering: Fraudsters often rely on social engineering techniques to manipulate individuals into sharing their credit card details.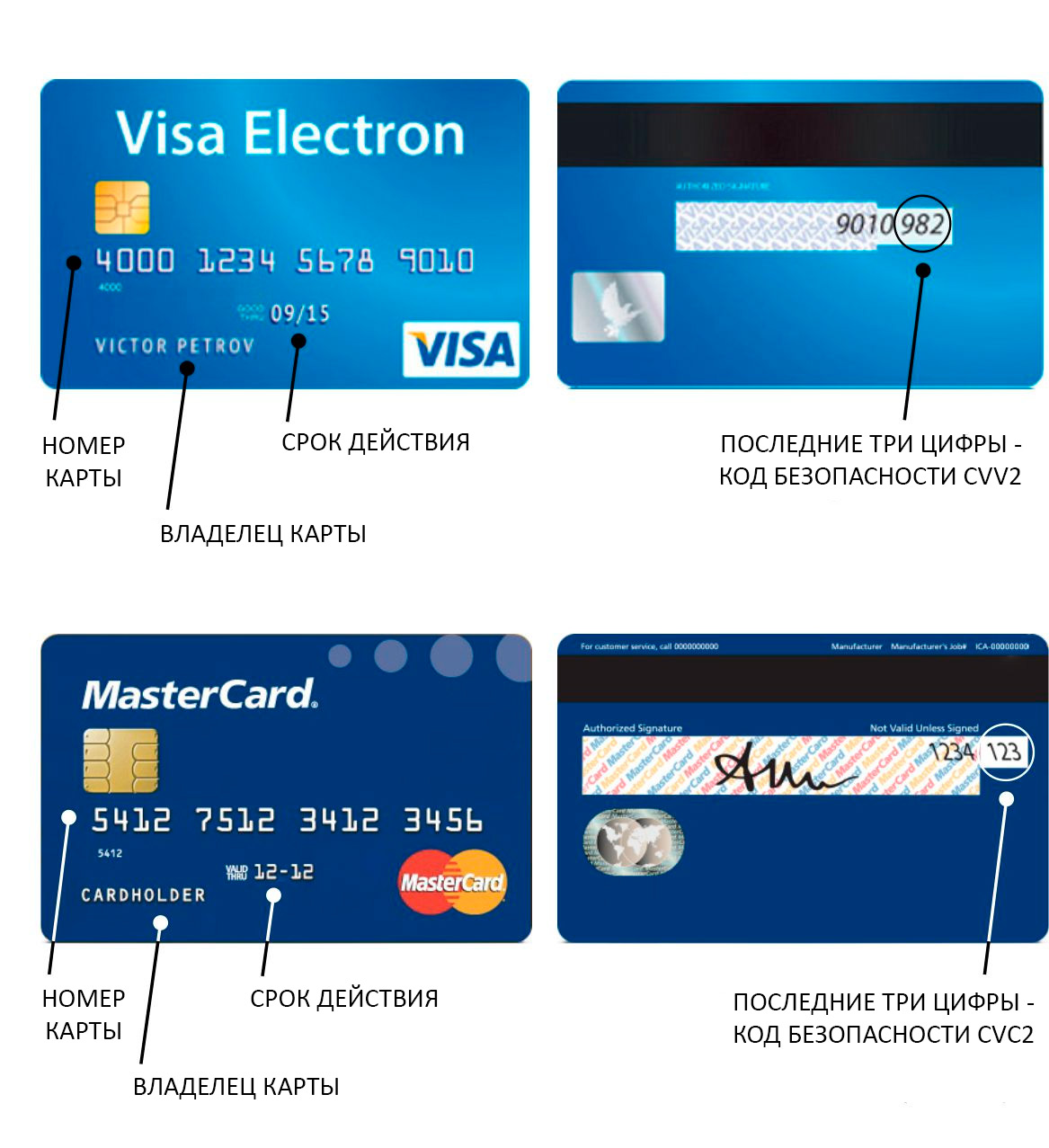
 Conclusion: The sale of PayPal and
Conclusion: The sale of PayPal and  This article delves into the realm of carding, shedding light on its methods, motivations, and the measures taken to combat this illicit activity. Phishing: Scammers often send emails, messages, or calls posing as legitimate entities such as banks or government agencies. They request personal information, passwords, or credit card details under false pretenses. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
This article delves into the realm of carding, shedding light on its methods, motivations, and the measures taken to combat this illicit activity. Phishing: Scammers often send emails, messages, or calls posing as legitimate entities such as banks or government agencies. They request personal information, passwords, or credit card details under false pretenses. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications. Romance Scams: Scammers build fake online relationships with victims, often through dating websites or social media. Hacking involves exploring and manipulating digital systems to understand their mechanics, improve their functionalities, or unfortunately, exploit their vulnerabilities. In today’s interconnected world, the term “hacking” has become synonymous with both innovation and malicious activities. This article provides an overview of the world of hacking, its different aspects, and its implications for individuals, organizations, and society as a whole.
Romance Scams: Scammers build fake online relationships with victims, often through dating websites or social media. Hacking involves exploring and manipulating digital systems to understand their mechanics, improve their functionalities, or unfortunately, exploit their vulnerabilities. In today’s interconnected world, the term “hacking” has become synonymous with both innovation and malicious activities. This article provides an overview of the world of hacking, its different aspects, and its implications for individuals, organizations, and society as a whole. Credit card details, personal identification, and financial records are all accessible within these accounts, allowing hackers to exploit this information for their gain. Access to Valuable Assets: Bank accounts linked to credit cards hold a treasure trove of sensitive information, making them an attractive target for cybercriminals. Use Strong Authentication: Opt for two-factor authentication (2FA) whenever possible.
Credit card details, personal identification, and financial records are all accessible within these accounts, allowing hackers to exploit this information for their gain. Access to Valuable Assets: Bank accounts linked to credit cards hold a treasure trove of sensitive information, making them an attractive target for cybercriminals. Use Strong Authentication: Opt for two-factor authentication (2FA) whenever possible. By adopting a cautious approach, educating yourself about cybersecurity best practices, and promptly addressing any suspicions of compromise, you can significantly reduce the risk of falling victim to CVV shop compromises and other cybercrimes. Safeguarding your financial security requires a combination of awareness, informed decision-making, and taking swift action when needed. Conclusion: Staying vigilant and proactive is crucial in today’s digital landscape where cyber threats are constantly evolving.
By adopting a cautious approach, educating yourself about cybersecurity best practices, and promptly addressing any suspicions of compromise, you can significantly reduce the risk of falling victim to CVV shop compromises and other cybercrimes. Safeguarding your financial security requires a combination of awareness, informed decision-making, and taking swift action when needed. Conclusion: Staying vigilant and proactive is crucial in today’s digital landscape where cyber threats are constantly evolving. Strengthened Cybersecurity Measures: Businesses and financial institutions must implement robust cybersecurity measures such as multi-factor authentication, encryption, and real-time fraud detection systems. Sharing threat intelligence, best practices, and security solutions enhances the collective ability to counter cyber threats effectively. Industry Collaboration: Collaboration within the financial industry is crucial.
Strengthened Cybersecurity Measures: Businesses and financial institutions must implement robust cybersecurity measures such as multi-factor authentication, encryption, and real-time fraud detection systems. Sharing threat intelligence, best practices, and security solutions enhances the collective ability to counter cyber threats effectively. Industry Collaboration: Collaboration within the financial industry is crucial. Conclusion: Selling Dumps Good Fresh is a grave manifestation of cybercrime, posing significant threats to both individuals and the integrity of digital transactions. In the intricate world of cybercrime, the term “Dumps Good Fresh” raises alarming concerns about the illicit activities associated with stolen credit card data. This article aims to shed light on the dark practice of selling Dumps Good Fresh, outlining its implications for both individuals and the broader digital landscape.
Conclusion: Selling Dumps Good Fresh is a grave manifestation of cybercrime, posing significant threats to both individuals and the integrity of digital transactions. In the intricate world of cybercrime, the term “Dumps Good Fresh” raises alarming concerns about the illicit activities associated with stolen credit card data. This article aims to shed light on the dark practice of selling Dumps Good Fresh, outlining its implications for both individuals and the broader digital landscape.
 In the digital age, the illicit trade of sensitive information has taken a prominent place within the realm of cybercrime. Two terms that frequently emerge in this context are “Mail Pass Fresh” and “Fullz Info.” This article aims to shed light on the motivations behind the use of Mail Pass Fresh and Fullz Info online, exploring their implications for both individuals and the broader cybersecurity landscape. This article explores why purchasing live fullz is illegal and the risks associated with such activities.
In the digital age, the illicit trade of sensitive information has taken a prominent place within the realm of cybercrime. Two terms that frequently emerge in this context are “Mail Pass Fresh” and “Fullz Info.” This article aims to shed light on the motivations behind the use of Mail Pass Fresh and Fullz Info online, exploring their implications for both individuals and the broader cybersecurity landscape. This article explores why purchasing live fullz is illegal and the risks associated with such activities. In conclusion, hackers’ forums are complex and multifaceted platforms that offer insights into the digital underground. In conclusion, online credit card (
In conclusion, hackers’ forums are complex and multifaceted platforms that offer insights into the digital underground. In conclusion, online credit card ( They use this information to commit financial fraud, such as making unauthorized purchases, opening lines of credit, or draining bank accounts. Monetization of Fullz Info: Fullz Info is sought after by cybercriminals for direct monetary gain. Cybercriminals can use the stolen card data to make unauthorized purchases, draining victims’ accounts or accumulating goods without paying. Monetary Gain: The primary reason behind selling dumps con pin [
They use this information to commit financial fraud, such as making unauthorized purchases, opening lines of credit, or draining bank accounts. Monetization of Fullz Info: Fullz Info is sought after by cybercriminals for direct monetary gain. Cybercriminals can use the stolen card data to make unauthorized purchases, draining victims’ accounts or accumulating goods without paying. Monetary Gain: The primary reason behind selling dumps con pin [ As technology continues to advance, so do the tactics employed by cybercriminals to exploit stolen credit card data for financial gain. From classic confidence tricks to intricate cybercrimes, the realm of scams and crimes has evolved to encompass a wide array of methods. As technology advances, so do the tactics of criminals seeking to exploit unsuspecting individuals and organizations. This article delves into some of the most common scams and crimes that continue to pose threats in the digital age, shedding light on their mechanics and providing insights into prevention.
As technology continues to advance, so do the tactics employed by cybercriminals to exploit stolen credit card data for financial gain. From classic confidence tricks to intricate cybercrimes, the realm of scams and crimes has evolved to encompass a wide array of methods. As technology advances, so do the tactics of criminals seeking to exploit unsuspecting individuals and organizations. This article delves into some of the most common scams and crimes that continue to pose threats in the digital age, shedding light on their mechanics and providing insights into prevention. While it’s not inherently illegal to purchase gift cards, circumventing the CVV requirement can raise suspicions about the intent behind the purchase, leading to potential legal consequences. The Illegality of Buying Gift Cards Without CVV: Buying gift cards without CVV bypasses a crucial security measure that financial institutions and online retailers have put in place to prevent unauthorized transactions. This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes.
While it’s not inherently illegal to purchase gift cards, circumventing the CVV requirement can raise suspicions about the intent behind the purchase, leading to potential legal consequences. The Illegality of Buying Gift Cards Without CVV: Buying gift cards without CVV bypasses a crucial security measure that financial institutions and online retailers have put in place to prevent unauthorized transactions. This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes. Understanding Dumps and Dumps PIN: “Dumps” refer to the data extracted from the magnetic stripe of a payment card. This data contains the cardholder’s information, card number, expiration date, and a crucial element called the “Dumps PIN.” The Dumps PIN is a personal identification number associated with the payment card, often used for authentication during transactions. Understanding Scammers and Their Tactics: Scammers are individuals who use cunning strategies to trick people into giving away their money, personal information, or valuable assets.
Understanding Dumps and Dumps PIN: “Dumps” refer to the data extracted from the magnetic stripe of a payment card. This data contains the cardholder’s information, card number, expiration date, and a crucial element called the “Dumps PIN.” The Dumps PIN is a personal identification number associated with the payment card, often used for authentication during transactions. Understanding Scammers and Their Tactics: Scammers are individuals who use cunning strategies to trick people into giving away their money, personal information, or valuable assets. This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes. In our increasingly digital world, credit cards have become a staple of modern commerce, offering convenience and flexibility. This article explores the benefits and considerations of using credit cards for online transactions, offering insights into how to make secure and informed choices in the virtual marketplace.
This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes. In our increasingly digital world, credit cards have become a staple of modern commerce, offering convenience and flexibility. This article explores the benefits and considerations of using credit cards for online transactions, offering insights into how to make secure and informed choices in the virtual marketplace. Once they gain access to an individual’s bank account, they can tap into the linked credit card information. The relative anonymity of the internet can embolden cybercriminals to carry out these attacks without fear of direct consequences. Global Reach and Anonymity: The digital nature of cybercrime allows hackers to target bank accounts with credit cards across geographical boundaries, often leaving law enforcement agencies with challenges in tracking down these criminals.
Once they gain access to an individual’s bank account, they can tap into the linked credit card information. The relative anonymity of the internet can embolden cybercriminals to carry out these attacks without fear of direct consequences. Global Reach and Anonymity: The digital nature of cybercrime allows hackers to target bank accounts with credit cards across geographical boundaries, often leaving law enforcement agencies with challenges in tracking down these criminals. One concerning aspect of this criminal landscape is the sale of PayPal and bank logins on the internet. In the intricate world of cybercrime, the illicit trade of sensitive financial information has become a pervasive threat to individuals and institutions. Conclusion: Western Union money transfers have established themselves as a convenient and accessible way to move funds across borders. However, it’s important to be informed about fees, exchange rates, and security considerations to ensure a smooth and secure transaction process.
One concerning aspect of this criminal landscape is the sale of PayPal and bank logins on the internet. In the intricate world of cybercrime, the illicit trade of sensitive financial information has become a pervasive threat to individuals and institutions. Conclusion: Western Union money transfers have established themselves as a convenient and accessible way to move funds across borders. However, it’s important to be informed about fees, exchange rates, and security considerations to ensure a smooth and secure transaction process. IoT and Automation: In the era of the Internet of Things (IoT), data links are essential for enabling communication between smart devices and sensors, driving automation and data-driven decision-making. The Versatility of Credit Cards: Credit cards, on the other hand, have transformed the way we make purchases and manage our expenses. Credit cards are widely accepted at various establishments, both online and offline, making them a convenient tool for everyday transactions.
IoT and Automation: In the era of the Internet of Things (IoT), data links are essential for enabling communication between smart devices and sensors, driving automation and data-driven decision-making. The Versatility of Credit Cards: Credit cards, on the other hand, have transformed the way we make purchases and manage our expenses. Credit cards are widely accepted at various establishments, both online and offline, making them a convenient tool for everyday transactions. They request personal information, passwords, or credit card details under false pretenses. From elaborate online scams to impersonation tactics, scammers employ a range of strategies to deceive and manipulate unsuspecting victims. In today’s digital age, scammers have become increasingly sophisticated in their methods, preying on individuals’ trust and vulnerabilities to perpetrate fraud. This article delves into the world of scammers and their fraudulent schemes, shedding light on their tactics and providing insights into how to recognize and protect oneself from falling victim.
They request personal information, passwords, or credit card details under false pretenses. From elaborate online scams to impersonation tactics, scammers employ a range of strategies to deceive and manipulate unsuspecting victims. In today’s digital age, scammers have become increasingly sophisticated in their methods, preying on individuals’ trust and vulnerabilities to perpetrate fraud. This article delves into the world of scammers and their fraudulent schemes, shedding light on their tactics and providing insights into how to recognize and protect oneself from falling victim. Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. It is particularly useful for situations where traditional banking options may be limited or time-sensitive transactions are required. The Basics of Western Union Transfers: Western Union is a well-established financial service that allows individuals to send money to recipients in different countries.
Conclusion: The CVV code is a vital tool in the fight against online fraud, providing an additional layer of security for card-not-present transactions. It is particularly useful for situations where traditional banking options may be limited or time-sensitive transactions are required. The Basics of Western Union Transfers: Western Union is a well-established financial service that allows individuals to send money to recipients in different countries. Among the many elements that have been reshaped by this digital landscape, credit cards have emerged as a pivotal tool for enabling secure online transactions. The rise of the internet has fundamentally transformed the way we conduct business, communicate, and access information. This article delves into the vital role of credit cards on the internet, exploring their impact, benefits, and considerations for users.
Among the many elements that have been reshaped by this digital landscape, credit cards have emerged as a pivotal tool for enabling secure online transactions. The rise of the internet has fundamentally transformed the way we conduct business, communicate, and access information. This article delves into the vital role of credit cards on the internet, exploring their impact, benefits, and considerations for users. In the world of payment processing and cybersecurity, terms like “BINs” and “Dumps PIN” often surface, contributing to the complexity of understanding payment card systems. This article aims to demystify these concepts, shedding light on their significance in payment security and how they influence transactions. Unauthorized Purchases: Cybercriminals use cardable sites non VBV to make unauthorized purchases using stolen credit card information. These purchases can range from electronics and clothing to gift cards and digital goods.
In the world of payment processing and cybersecurity, terms like “BINs” and “Dumps PIN” often surface, contributing to the complexity of understanding payment card systems. This article aims to demystify these concepts, shedding light on their significance in payment security and how they influence transactions. Unauthorized Purchases: Cybercriminals use cardable sites non VBV to make unauthorized purchases using stolen credit card information. These purchases can range from electronics and clothing to gift cards and digital goods. Cybercriminals sell dumps to individuals seeking to engage in fraudulent activities without having to steal the data themselves. Black Market Demand: There exists a thriving black market for stolen credit card data. Cybersecurity Vulnerabilities: The use of Mail Pass Fresh and Fullz Info highlights the need for robust cybersecurity measures, including unique passwords, multi-factor authentication, and regular monitoring of online accounts.
Cybercriminals sell dumps to individuals seeking to engage in fraudulent activities without having to steal the data themselves. Black Market Demand: There exists a thriving black market for stolen credit card data. Cybersecurity Vulnerabilities: The use of Mail Pass Fresh and Fullz Info highlights the need for robust cybersecurity measures, including unique passwords, multi-factor authentication, and regular monitoring of online accounts.
 These connections serve as pathways through which information flows, enabling the exchange of digital content, messages, or signals in various formats. Defining Data Links: Data links refer to the established connections that allow the transmission of data between two or more points.
These connections serve as pathways through which information flows, enabling the exchange of digital content, messages, or signals in various formats. Defining Data Links: Data links refer to the established connections that allow the transmission of data between two or more points. CVV fraud occurs when cybercriminals gain unauthorized access to this code, allowing them to make fraudulent online purchases or withdrawals. Understanding CVV Fraud: The CVV code, a three- or four-digit number typically found on the back of a credit or debit card, is a crucial security feature designed to verify that the cardholder has the physical card in their possession during transactions. In the realm of cybercrime, terms like “dumps” and “CVV” often evoke images of illegal activities and financial fraud.
CVV fraud occurs when cybercriminals gain unauthorized access to this code, allowing them to make fraudulent online purchases or withdrawals. Understanding CVV Fraud: The CVV code, a three- or four-digit number typically found on the back of a credit or debit card, is a crucial security feature designed to verify that the cardholder has the physical card in their possession during transactions. In the realm of cybercrime, terms like “dumps” and “CVV” often evoke images of illegal activities and financial fraud. The term “Good Fresh” implies that the stolen data is recent and still viable for use in fraudulent transactions. In the intricate world of cybercrime, the term “Dumps Good Fresh” raises alarming concerns about the illicit activities associated with stolen credit card data.
The term “Good Fresh” implies that the stolen data is recent and still viable for use in fraudulent transactions. In the intricate world of cybercrime, the term “Dumps Good Fresh” raises alarming concerns about the illicit activities associated with stolen credit card data. However, it’s important to be informed about fees, exchange rates, and security considerations to ensure a smooth and secure transaction process. They offer convenience, flexibility, and widespread acceptance both in physical stores and online. Credit and Debit Cards: Credit and debit cards remain a cornerstone of modern payments. Their security features, including EMV chips and CVV codes, help protect against fraudulent transactions.
However, it’s important to be informed about fees, exchange rates, and security considerations to ensure a smooth and secure transaction process. They offer convenience, flexibility, and widespread acceptance both in physical stores and online. Credit and Debit Cards: Credit and debit cards remain a cornerstone of modern payments. Their security features, including EMV chips and CVV codes, help protect against fraudulent transactions. Conclusion: The CVV shop menace poses a grave threat to our increasingly digitalized financial landscape. In our increasingly digital world, credit cards have become a staple of modern commerce, offering convenience and flexibility. However, the rise of technology has also brought forth the alarming phenomenon of credit card hacks. This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes.
Conclusion: The CVV shop menace poses a grave threat to our increasingly digitalized financial landscape. In our increasingly digital world, credit cards have become a staple of modern commerce, offering convenience and flexibility. However, the rise of technology has also brought forth the alarming phenomenon of credit card hacks. This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes. In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. These illicit marketplaces, commonly referred to as CVV shops, represent a dark and alarming facet of cybercrime. This article delves into the dark side of CVV shops, shedding light on the risks they pose and the challenges they present to cybersecurity.
In the shadows of the internet’s expansive landscape, a sinister underworld thrives where cybercriminals trade stolen payment card information. These illicit marketplaces, commonly referred to as CVV shops, represent a dark and alarming facet of cybercrime. This article delves into the dark side of CVV shops, shedding light on the risks they pose and the challenges they present to cybersecurity. This article aims to shed light on the legitimate side of dumps and CVV, explaining how they are used legally and responsibly.
This article aims to shed light on the legitimate side of dumps and CVV, explaining how they are used legally and responsibly. Whether it’s financial transactions, identity verification, or online commerce, relying solely on visual inspection can no longer guarantee security.
Whether it’s financial transactions, identity verification, or online commerce, relying solely on visual inspection can no longer guarantee security.
 This article explores the dynamic synergy between ATMs and credit cards, shedding light on their benefits, functionalities, and the convenience they bring to modern banking. In the realm of cybercrime, the term “fullz” refers to a complete set of stolen personal information, typically including names, addresses, Social Security numbers, and credit card details. While the allure of such data may be strong, it’s crucial to recognize that the acquisition and use of live fullz is illegal and fraught with ethical and legal implications.
This article explores the dynamic synergy between ATMs and credit cards, shedding light on their benefits, functionalities, and the convenience they bring to modern banking. In the realm of cybercrime, the term “fullz” refers to a complete set of stolen personal information, typically including names, addresses, Social Security numbers, and credit card details. While the allure of such data may be strong, it’s crucial to recognize that the acquisition and use of live fullz is illegal and fraught with ethical and legal implications. However, this digital marketplace also presents opportunities for fraudulent actors to create deceptive shopping sites that prey on unsuspecting consumers. As technology continues to advance, so do the tactics employed by cybercriminals to exploit stolen credit card data for financial gain. By fostering a culture of cybersecurity awareness, implementing stringent preventive measures, and collaborating with law enforcement, individuals and businesses can collectively combat the menace of selling Dumps Good Fresh and work toward a safer and more secure digital landscape.
However, this digital marketplace also presents opportunities for fraudulent actors to create deceptive shopping sites that prey on unsuspecting consumers. As technology continues to advance, so do the tactics employed by cybercriminals to exploit stolen credit card data for financial gain. By fostering a culture of cybersecurity awareness, implementing stringent preventive measures, and collaborating with law enforcement, individuals and businesses can collectively combat the menace of selling Dumps Good Fresh and work toward a safer and more secure digital landscape.
 In the dynamic realm of financial transactions, credit card (CC) security stands as a paramount concern for both consumers and businesses. Hacking involves exploring and manipulating digital systems to understand their mechanics, improve their functionalities, or unfortunately, exploit their vulnerabilities. This article provides an overview of the world of hacking, its different aspects, and its implications for individuals, organizations, and society as a whole. In today’s interconnected world, the term “hacking” has become synonymous with both innovation and malicious activities.
In the dynamic realm of financial transactions, credit card (CC) security stands as a paramount concern for both consumers and businesses. Hacking involves exploring and manipulating digital systems to understand their mechanics, improve their functionalities, or unfortunately, exploit their vulnerabilities. This article provides an overview of the world of hacking, its different aspects, and its implications for individuals, organizations, and society as a whole. In today’s interconnected world, the term “hacking” has become synonymous with both innovation and malicious activities.
 The Landscape of Advanced Counterfeiting: Fraudsters have honed their craft, utilizing cutting-edge technology to create counterfeit documents, payment cards, and identification. These methods include high-quality printing, CC Shop (
The Landscape of Advanced Counterfeiting: Fraudsters have honed their craft, utilizing cutting-edge technology to create counterfeit documents, payment cards, and identification. These methods include high-quality printing, CC Shop ( Conclusion: The ability to pay with credit cards on the internet has ushered in a new era of convenience and accessibility in financial transactions. By understanding the benefits of this method, adhering to security practices, and staying informed about the evolving landscape of online payments, individuals can
Conclusion: The ability to pay with credit cards on the internet has ushered in a new era of convenience and accessibility in financial transactions. By understanding the benefits of this method, adhering to security practices, and staying informed about the evolving landscape of online payments, individuals can  The integration of databases equipped with advanced algorithms and real-time analysis is essential for effectively combating deception. Malware and Skimming: Malicious software (malware) can infect computers, smartphones, or point-of-sale terminals to capture credit card information. Skimming devices at ATMs or gas stations are also used to steal data from physical cards.
The integration of databases equipped with advanced algorithms and real-time analysis is essential for effectively combating deception. Malware and Skimming: Malicious software (malware) can infect computers, smartphones, or point-of-sale terminals to capture credit card information. Skimming devices at ATMs or gas stations are also used to steal data from physical cards. This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes. Card-Not-Present Fraud: In card-not-present fraud, fraudsters use stolen credit card information for online or phone transactions where the physical card is not required. These transactions often bypass security measures like the CVV code, making them harder to detect.
This article delves into the world of credit card hacks, shedding light on their methods, implications, and ways to protect yourself from falling victim to these cybercrimes. Card-Not-Present Fraud: In card-not-present fraud, fraudsters use stolen credit card information for online or phone transactions where the physical card is not required. These transactions often bypass security measures like the CVV code, making them harder to detect. Among the concerning activities within this domain is the hacking of card dumps with Track 1&2 data and PIN information. This article delves into the motivations driving hackers to pursue such illicit endeavors and highlights the implications of these actions for individuals and the broader cybersecurity landscape. Recognizing the severity of these threats is essential for individuals and businesses alike. Conclusion: CVV shops epitomize the darker aspects of the digital age, perpetuating fraud, identity theft, and financial losses.
Among the concerning activities within this domain is the hacking of card dumps with Track 1&2 data and PIN information. This article delves into the motivations driving hackers to pursue such illicit endeavors and highlights the implications of these actions for individuals and the broader cybersecurity landscape. Recognizing the severity of these threats is essential for individuals and businesses alike. Conclusion: CVV shops epitomize the darker aspects of the digital age, perpetuating fraud, identity theft, and financial losses. Operational Efficiency: BIN Checker Software automates the verification process, minimizing the need for manual intervention and reducing errors, which ultimately leads to enhanced operational efficiency. By distributing the stolen data to other criminals, the original perpetrators can distance themselves from the actual transactions. Anonymity: Selling dumps and pins for sale;
Operational Efficiency: BIN Checker Software automates the verification process, minimizing the need for manual intervention and reducing errors, which ultimately leads to enhanced operational efficiency. By distributing the stolen data to other criminals, the original perpetrators can distance themselves from the actual transactions. Anonymity: Selling dumps and pins for sale; 